Join the discussion
Question 1/181
Refer to exhibit. Which two descriptions of the configurations of the Cisco FirePOWER Services module are true? (Choose two)
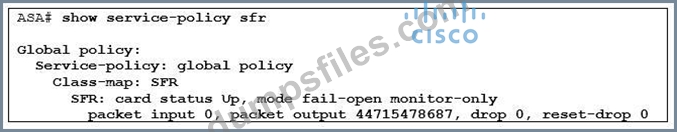

Correct Answer: C,D
Add Comments
- Other Question (181q)
- Q1. Refer to exhibit. Which two descriptions of the configurations of the Cisco FirePOWER Serv...
- Q2. A network engineer is deploying a pair of Cisco Secure Firewall Threat Defense devices man...
- Q3. Which Cisco FMC report gives the analyst information about the ports and protocols that ar...
- Q4. Which two statements are valid regarding the licensing model used on Cisco Secure Firewall...
- Q5. An engineer is configuring two new Cisco FTD devices to replace the existing high availabi...
- Q6. What is the disadvantage of setting up a site-to-site VPN in a clustered-units environment...
- Q7. An engineer must deny ICMP traffic to the networks of separate departments that use Cisco ...
- Q8. A security engineer must integrate an external feed containing STIX/TAXII data with Cisco ...
- Q9. An engineer must create an access control policy on a Cisco Secure Firewall Threat Defense...
- Q10. Which command-line mode is supported from the Cisco Firepower Management Center CLI?...
- Q11. A network administrator needs to create a policy on Cisco Firepower to fast-path traffic t...
- Q12. A security engineer sees an alert on Cisco Secure Endpoint console showing a malicious ver...
- Q13. An engineer wants to change an existing transparent Cisco FTD to routed mode. The device c...
- Q14. The network administrator wants to enhance the network security posture by enabling machin...
- Q15. An administrator is configuring the interface of a Cisco Secure Firewall Threat Defense fi...
- Q16. An engineer is troubleshooting an intermittent connectivity issue on a Cisco Secure Firewa...
- Q17. An engineer has been tasked with performing an audit of network objects to determine which...
- Q18. A network administrator is reviewing a weekly scheduled attacks risk report and notices a ...
- Q19. An engineer must implement static route tracking on Cisco Secure Firewall Threat Defense a...
- Q20. There is an increased amount of traffic on the network and for compliance reasons, managem...
- Q21. A Cisco Secure Firewall Threat Defense device is configured in inline IPS mode to inspect ...
- Q22. Which two OSPF routing features are configured in Cisco FMC and propagated to Cisco FTD? (...
- Q23. A security engineer is deploying a pair of primary and secondary Cisco FMC devices. The se...
- Q24. Which protocol establishes network redundancy in a switched Firepower device deployment?...
- Q25. On Cisco Firepower Management Center, which policy is used to collect health modules alert...
- Q26. A Cisco FTD device is running in transparent firewall mode with a VTEP bridge group member...
- Q27. Refer to the exhibit. An engineer is modifying an access control pokey to add a rule to in...
- Q28. A company is in the process of deploying intrusion prevention with Cisco FTDs managed by a...
- Q29. An engineer is setting up a new Cisco Secure Firewall Threat Defense appliance to replace ...
- Q30. What is the difference between inline and inline tap on Cisco Firepower?...
- Q31. When a Cisco FTD device is configured in transparent firewall mode, on which two interface...
- Q32. An engineer must export a packet capture from Cisco Secure Firewall Management Center to a...
- Q33. Which object type supports object overrides?
- Q34. A network administrator is reviewing a packet capture. The packet capture from inside of C...
- Q35. An engineer must build redundancy into the network and traffic must continuously flow if a...
- Q36. A security engineer manages a firewall console and an endpoint console and finds it challe...
- Q37. An engineer must deploy a Cisco FTD appliance via Cisco FMC to span a network segment to d...
- Q38. A security engineer is configuring an Access Control Policy for multiple branch locations....
- Q39. A mid-sized company is experiencing higher network bandwidth utilization due to a recent a...
- Q40. A security engineer must add a new policy to block UDP traffic to one server. The engineer...
- Q41. An administrator must fix a network problem whereby traffic from the inside network to a w...
- Q42. Which file format can standard reports from Cisco Secure Firewall Management Center be dow...
- Q43. Which Firepower feature allows users to configure bridges in routed mode and enables devic...
- Q44. A network administrator is configuring a Cisco AMP public cloud instance and wants to capt...
- Q45. With Cisco FTD software, which interface mode must be configured to passively receive traf...
- Q46. A company is deploying Cisco Secure Firewall Threat Defense with IPS. What must be impleme...
- Q47. What is a characteristic of bridge groups on a Cisco FTD?...
- Q48. An engineer must change the mode of a Cisco Secure Firewall Threat Defense (FTD) firewall ...
- Q49. When an engineer captures traffic on a Cisco FTD to troubleshoot a connectivity problem, t...
- Q50. Which two routing options are valid with Cisco Firepower Threat Defense? (Choose two.)...
- Q51. Which action must be taken to permit communication between a bridge group and routed inter...
- Q52. A network engineer must provide redundancy between two Cisco FTD devices. The redundancy c...
- Q53. When using Cisco AMP for Networks, which feature copies a file to the Cisco AMP cloud for ...
- Q54. A network administrator cannot select the link to be used for failover when configuring an...
- Q55. What is the benefit of selecting the trace option for packet capture?...
- Q56. Which Cisco deployment architectures support Clustering? (Choose 2)....
- Q57. An organization has a compliancy requirement to protect servers from clients, however, the...
- Q58. What Software can be installed on the Cisco 4100 series appliance? (Choose two)...
- Q59. An engineer must investigate a connectivity issue from an endpoint behind a Cisco FTD devi...
- Q60. An engineer must reconfigure an NTP server on an IPSv device that is managed by using Cisc...
- Q61. An engineer integrates Cisco FMC and Cisco ISE using pxGrid. Which role is assigned for Ci...
- Q62. An organization wants to secure traffic from their branch office to the headquarter buildi...
- Q63. A Cisco FTD has two physical interfaces assigned to a BVI. Each interface is connected to ...
- Q64. The event dashboard within the Cisco FMC has been inundated with low priority intrusion dr...
- Q65. An engineer configures a network discovery policy on Cisco FMC. Upon configuration, it is ...
- Q66. The administrator notices that there is malware present with an .exe extension and needs t...
- Q67. An engineer needs to configure remote storage on Cisco FMC. Configuration backups must be ...
- Q68. A company has many Cisco FTD devices managed by a Cisco FMC. The security model requires t...
- Q69. Users report that Cisco Duo 2FA fails when they attempt to connect to the VPN on a Cisco S...
- Q70. Refer to the exhibit. An engineer generates troubleshooting files in Cisco Secure Firewall...
- Q71. Which two remediation options are available when Cisco FMC is integrated with Cisco ISE? (...
- Q72. Which action must be taken to configure an isolated bridge group for IRB mode on a Cisco S...
- Q73. A security engineer is deploying Cisco Secure Endpoint to detect a zero day malware attack...
- Q74. An engineer is configuring a Cisco Secure Firewall Threat Defense device and wants to crea...
- Q75. An organization has seen a lot of traffic congestion on their links going out to the inter...
- Q76. What is the result of specifying of QoS rule that has a rate limit that is greater than th...
- Q77. An engineer is creating an URL object on Cisco FMC How must it be configured so that the o...
- Q78. When deploying a Cisco ASA Firepower module, an organization wants to evaluate the content...
- Q79. Which two statements about bridge-group interfaces in Cisco FTD are true? (Choose two.)...
- Q80. Which two dynamic routing protocols are supported in FirePower Threat Defense v6.0? (Choos...
- Q81. After using Firepower for some time and learning about how it interacts with the network, ...
- Q82. An organization is using a Cisco FTD and Cisco ISE to perform identity-based access contro...
- Q83. A network engineer must configure an existing firewall to have a NAT configuration. The ne...
- Q84. An engineer must configure the firewall to monitor traffic within a single subnet without ...
- Q85. A security engineer is adding three Cisco FTD devices to a Cisco FMC. Two of the devices h...
- Q86. An engineer must implement Cisco Secure Firewall transparent mode due to a new server rece...
- Q87. What is a functionality of port objects in Cisco FMC?...
- Q88. A security engineer must configure policies for a recently deployed Cisco FTD. The securit...
- Q89. A network engineer must configure IPS mode on a Secure Firewall Threat Defense device to i...
- Q90. An external vendor is reporting that they are unable to access an ordering website hosted ...
- Q91. What is a feature of Cisco AMP private cloud?
- Q92. A network administrator is configuring Snort inspection policies and is seeing failed depl...
- Q93. In which two ways do access control policies operate on a Cisco Firepower system? (Choose ...
- Q94. A network engineer is tasked with minimising traffic interruption during peak traffic lime...
- Q95. Which two features of Cisco AMP for Endpoints allow for an uploaded file to be blocked? (C...
- Q96. An engineer must export a packet capture from Cisco Secure Firewall Management Center to a...
- Q97. Which protocol is needed to exchange threat details in rapid threat containment on Cisco F...
- Q98. Which rule action is only available in Snort 3?...
- Q99. What must be implemented on Cisco Firepower to allow multiple logical devices on a single ...
- Q100. What is the result when two users modify a VPN policy at the same time on a Cisco Secure F...
- Q101. An engineer is using the configure manager add <FMC IP> Cisc404225383 command to add...
- Q102. A security engineer found a suspicious file from an employee email address and is trying t...
- Q103. An engineer is deploying a Cisco ASA Secure Firewall module. The engineer must be able to ...
- Q104. Which option is the main function of Cisco Firepower impact flags?...
- Q105. An organization has a Cisco FTD that uses bridge groups to pass traffic from the inside in...
- Q106. An engineer is deploying the Cisco Firepower NGIPSv for vMware. Which two aspects are unsu...
- Q107. An engineer is tasked with configuring a custom intrusion rule on Cisco Secure Firewall Ma...
- Q108. Remote users who connect via Cisco AnyConnect to the corporate network behind a Cisco FTD ...
- Q109. What is the advantage of having Cisco Firepower devices send events to Cisco Threat respon...
- Q110. With Cisco AMP for Endpoints, which option shows a list of all files that have been execut...
- Q111. An engineer is troubleshooting a file that is being blocked by a Cisco FTD device on the n...
- Q112. What is the maximum bit size that Cisco FMC supports for HTTPS certificates?...
- Q113. An engineer is configuring a Cisco FTD device to place on the Finance VLAN to provide addi...
- Q114. Drag and Drop Question Drag and drop the steps to restore an automatic device registration...
- Q115. administrator is configuring SNORT inspection policies and is seeing failed deployment mes...
- Q116. An engineer must define a URL object on Cisco FMC. What is the correct method to specify t...
- Q117. Which two feature does Cisco Trust Anchor support? (Choose two.)...
- Q118. What is a result of enabling Cisco FTD clustering?...
- Q119. Which feature within the Cisco FMC web interface allows for detecting, analyzing and block...
- Q120. An administrator is adding a QoS policy to a Cisco FTD deployment. When a new rule is adde...
- Q121. What are 2 types or forms of suppression on a FirePower policy (or FTD)?...
- Q122. Refer to the exhibit. And engineer is analyzing the Attacks Risk Report and finds that the...
- Q123. With Cisco FTD integrated routing and bridging, which interface does the bridge group use ...
- Q124. Refer to the exhibit. A Cisco Secure Firewall Threat Defense (FTD) device is deployed in i...
- Q125. A network administrator reviews the attack risk report and notices several low-impact atta...
- Q126. A network administrator registered a new FTD to an existing FMC. The administrator cannot ...
- Q127. Drag and Drop Question Drag and drop the configuration steps from the left into the sequen...
- Q128. An engineer is deploying failover capabilities for a pair of Cisco Secure Firewall devices...
- Q129. An engineer is attempting to add a new FTD device to their FMC behind a NAT device with a ...
- Q130. Which policy rule is included in the deployment of a local DMZ during the initial deployme...
- Q131. A network administrator notices that remote access VPN users are not reachable from inside...
- Q132. A company wants a solution to aggregate the capacity of two Cisco FTD devices to make the ...
- Q133. Refer to the exhibit. An engineer analyzes a Network Risk Report from Cisco Secure Firewal...
- Q134. Which process should be checked when troubleshooting registration issues between Cisco FMC...
- Q135. Drag and Drop Question Refer to the exhibit. An engineer must configure a connection on a ...
- Q136. An engineer is configuring URL filtering for a Cisco FTD device in Cisco FMC. Users must r...
- Q137. Upon detecting a flagrant threat on an endpoint, which two technologies instruct Cisco Ide...
- Q138. A network administrator notices that SI events are not being updated The Cisco FTD device ...
- Q139. An organization recently implemented a transparent Cisco FTD in their network. They must e...
- Q140. A software development company hosts the website https://dev.company.com for contractors t...
- Q141. A network administrator wants to block traffic to a known malware site at https://www.bads...
- Q142. When packet capture is used on a Cisco Secure Firewall Threat Defense device and the packe...
- Q143. An engineer is tasked with deploying an internal perimeter firewall that will support mult...
- Q144. A network administrator must create an EtherChannel interface on a new Cisco Firepower 930...
- Q145. A connectivity issue is occurring between a client and a server which are communicating th...
- Q146. A network administrator is configuring an FTD in transparent mode. A bridge group is set u...
- Q147. Which Cisco Advanced Malware Protection for Endpoints policy is used only for monitoring e...
- Q148. An engineer is attempting to create a new dashboard within the Cisco FMC to have a single ...
- Q149. When do you need the file-size command option during troubleshooting with packet capture?...
- Q150. An engineer must investigate a connectivity issue by using Cisco Secure Firewall Managemen...
- Q151. Refer to the exhibit. A network engineer is analyzing a Network Risk Report generated in C...
- Q152. Which group within Cisco does the Threat Response team use for threat analysis and researc...
- Q153. A security engineer must configure a Cisco FTD appliance to inspect traffic coming from th...
- Q154. In a multi-tenant deployment where multiple domains are in use. Which update should be app...
- Q155. An engineer is configuring a cisco FTD appliance in IPS-only mode and needs to utilize fai...
- Q156. What is an advantage of adding multiple inline interface pairs to the same inline interfac...
- Q157. Which description of the file trajectory feature in Cisco AMP is true?...
- Q158. How many report templates does the Cisco Firepower Management Center support?...
- Q159. A network administrator is deploying a Cisco IPS appliance and needs it to operate initial...
- Q160. With a recent summer time change, system logs are showing activity that occurred to be an ...
- Q161. Which feature is supported by IRB on Cisco FTD devices?...
- Q162. Refer to the exhibit. An engineer is configuring access control rules on a Cisco Secure Fi...
- Q163. An engineer wants to connect a single IP subnet through a Cisco FTD firewall and enforce p...
- Q164. An engineer is investigating connectivity problems on Cisco Firepower for a specific SGT. ...
- Q165. Which command must be run to generate troubleshooting files on an FTD?...
- Q166. An engineer currently has a Cisco FTD device registered to the Cisco FMC and is assigned t...
- Q167. A consultant is working on a project where the customer is upgrading from a single Cisco F...
- Q168. A network administrator is reviewing a monthly advanced malware risk report and notices a ...
- Q169. A security engineer needs to configure a network discovery policy on a Cisco FMC appliance...
- Q170. Refer to the exhibit. An engineer is troubleshooting connectivity issues over a VPN tunnel...
- Q171. Which limitation applies to Cisco Firepower Management Center dashboards in a multidomain ...
- Q172. Which two TCP ports can allow the Cisco Firepower Management Center to communication with ...
- Q173. A network administrator is setting up a Cisco Secure Firewall Threat Defense to peer via B...
- Q174. An engineer is configuring Cisco FMC and wants to limit the time allowed for processing pa...
- Q175. What is a purpose of the network analysis policy on a Cisco Firepower NGIPS?...
- Q176. An engineer is configuring a custom application detector for HTTP traffic and wants to imp...
- Q177. An organization is migrating their Cisco ASA devices running in multicontext mode to Cisco...
- Q178. Which two conditions are necessary for high availability to function between two Cisco FTD...
- Q179. A network administrator is implementing an active/passive high availability Cisco FTD pair...
- Q180. Which license type is required on Cisco ISE to integrate with Cisco FMC pxGrid?...
- Q181. An engineer installs a Cisco FTD device and wants to inspect traffic within the same subne...


