Join the discussion
Question 1/200
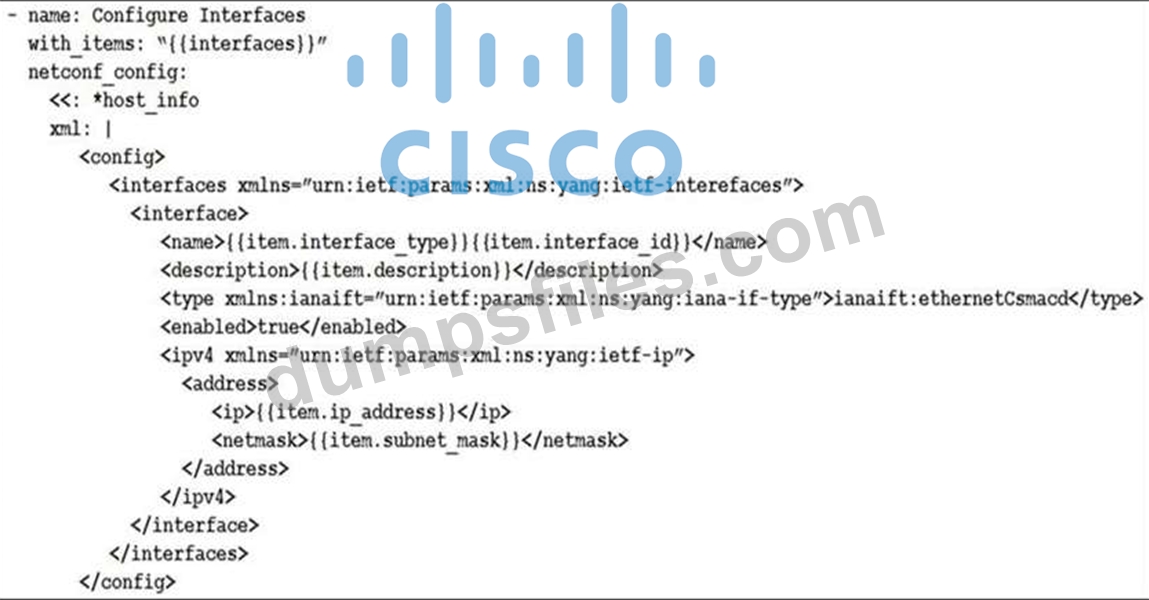
Refer to the exhibit. The Ansible playbook is using the netconf_module to configure an interface using a YANG model. As part of this workflow, which YANG models augment the interface?
Correct Answer: B
Section: Infrastructure and Automation
Explanation/Reference:
Explanation/Reference:
Add Comments
- Other Question (200q)
- Q1. (Exhibit) Refer to the exhibit. The Ansible playbook is using the netconf_module to config...
- Q2. Drag and drop the steps from the left into the correct sequence on the right to describe h...
- Q3. Refer to the exhibit. The self-service Webex Teams bot is failing when many users attempt ...
- Q4. Which two statements describe the traits of an asynchronous API call? (Choose two.)...
- Q5. A developer is creating a Python function that adds network engineers to a Webex room to t...
- Q6. Refer to the exhibit. (Exhibit) A) (Exhibit) B) (Exhibit) C) (Exhibit) D) (Exhibit)...
- Q7. Drag and drop the steps from the left into the correct sequence on the right to describe h...
- Q8. Refer to the exhibit. (Exhibit) Drag and drop the code snippets from the left onto the ite...
- Q9. (Exhibit) Refer to the exhibit above and click on the resource tabs in the top left corner...
- Q10. Which type of file is created from issued intermediate, root, and primary certificates for...
- Q11. Meraki Dashboard API Response Response Status Code200 Response Link Header <https://n6....
- Q12. (Exhibit) Refer to the exhibit above and click on the tab in the top left corner to view a...
- Q13. Refer to the exhibit. (Exhibit) A developer is creating a Python script to use the Webex T...
- Q14. Refer to the exhibit. A developer is creating a Python script to use the Webex Teams REST ...
- Q15. (Exhibit) Refer to the exhibit above and click on the IETF Routing tab in the top left cor...
- Q16. There is a requirement to securely store unique usernames and passwords. Given a valid use...
- Q17. Refer to the exhibit. (Exhibit) Drag and drop the code snippets from the left onto the ite...
- Q18. An engineer is developing a web-based application that will be used as a central repositor...
- Q19. A developer has created an application based on customer requirements. The customer needs ...
- Q20. Drag and drop the steps on the left into the order on the right for an end-user to access ...
- Q21. Drag and drop the code from the bottom onto the box where the code is missing in the diagr...
- Q22. A cloud native project is being worked on in which all source code and dependencies are wr...
- Q23. An application is developed in order to communicate with Cisco Webex. For reporting, the a...
- Q24. What is a characteristic of a monolithic architecture?...
- Q25. Drag and drop the git commands from the left into the correct order on the right to create...
- Q26. (Exhibit) Refer to the exhibit above and click on the resource tabs in the top left corner...
- Q27. (Exhibit) Refer to the exhibit above and click on the resource tabs in the top left corner...
- Q28. Refer tothe exhibit. (Exhibit) Two editors are concurrently updating an article's headline...
- Q29. Refer to the exhibit. (Exhibit) Drag and drop the steps from the left into the correct ord...
- Q30. Refer to the exhibit. (Exhibit) This snippet of a script has recently started exiting abno...
- Q31. (Exhibit) Refer to the exhibit. Drag and drop the code snippets from the left onto the ite...
- Q32. A heterogeneous network of vendors and device types needs automating for better efficiency...
- Q33. Refer to the exhibit. (Exhibit) An engineer writes a script to retrieve data from a REST A...
- Q34. Refer to the exhibit. (Exhibit) Python threading allows a developer to have different part...
- Q35. Drag and drop the code snippets from the bottom onto the boxes where the code is missing t...
- Q36. A network engineer needs to retrieve interface data using the Cisco IOS XE YANG Model. Dra...
- Q37. A cloud native project is being worked on in which all source code and dependencies are wr...
- Q38. Refer to the exhibit. (Exhibit) An application has been created to serve a whole enterpris...
- Q39. Which two statements describe advantages of static code analysis over unit tests? (Choose ...
- Q40. Refer to the exhibit. (Exhibit) Which parameter is missing from the JSON response to confi...
- Q41. Refer to the exhibit. (Exhibit) Which code snippet is required in the headers to successfu...
- Q42. Refer to the exhibit. (Exhibit) A Python developer is creating a wireless network device i...
- Q43. Refer to the exhibit. (Exhibit) The Ansible playbook is using the netconf_module to config...
- Q44. Which Puppet manifest changes the NTP server and generates the traffic from VLAN 15? A) (E...
- Q45. Refer to the exhibit. (Exhibit) Drag and drop the code snippets from the bottom onto the b...
- Q46. Refer to the exhibit. (Exhibit) The YAML represented is using the ios_vrf module. As part ...
- Q47. An engineer must access multiple bots that are running in an internal infrastructure. A di...
- Q48. Refer to the exhibit. (Exhibit) Drag and drop the steps from the left into the correct ord...
- Q49. Refer to the exhibit. (Exhibit) Which additional line results in the output of Test 1 upon...
- Q50. Refer to the exhibit. (Exhibit) An engineer needs to change the IP address via RESTCOMF on...
- Q51. Which snippet presents the correct API call to configure, secure, and enable an SSID using...
- Q52. Drag and drop the code from the bottom onto the box where the code is missing in the Pytho...
- Q53. Refer to the exhibit. (Exhibit) Which additional line results in the output of Test 1 upon...
- Q54. DRAG DROP (Exhibit) Refer to the exhibit. Drag and drop the correct parts of the Dockerfil...
- Q55. (Exhibit) Refer to the exhibit above and click on the tab in the top left corner to view a...
- Q56. Refer to the exhibit. (Exhibit) Drag and drop the code snippets from the left onto the ite...
- Q57. What is the gRPC Network Management Interface protocol?...
- Q58. Refer to the exhibit. (Exhibit) Interface Lookback 1 must be created with IP address 10.30...
- Q59. Refer to the exhibit. (Exhibit) Which key value pair from the ios_ntp Ansible module creat...
- Q60. The UCS Python SDK includes modules for Service Profile template creation. Which two UCS S...
- Q61. Refer to the exhibit. (Exhibit) An Intersight API is being used to query RackUnit resource...
- Q62. A developer is working on a new feature in a branch named 'newfeay000222118' and the curre...
- Q63. (Exhibit) Refer to the exhibit. Drag and drop the code snippets from the left onto the ite...
- Q64. A developer is creating a Python script to catch errors using REST API calls and to aid in...
- Q65. Refer to the exhibit. (Exhibit) The YAML represented is using the ios_vrf module. As part ...
- Q66. Drag and Drop Question Refer to the exhibit. Python threading allows a developer to have d...
- Q67. A bot has been created, called "386231131", to respond to alarm messages. A developer is n...
- Q68. A local data center deployment using Cisco NX-OS switches is scaling and requires automati...
- Q69. Drag and drop the descriptions from the left onto the related OAuth-defined roles on the r...
- Q70. An application uses OAuth to get access to several API resources on behalf of an end user....
- Q71. (Exhibit) Refer to the exhibit. Drag and drop the code snippets from the left onto the ite...
- Q72. Refer to the exhibit. (Exhibit) Which configuration of method and parameter retrieves the ...
- Q73. Drag and drop the git commands from the left into the correct order on the right to create...
- Q74. An application is being built to collect and display telemetry streaming data. Drag and dr...
- Q75. A developer has completed the implementation of a REST API, but when it is executed, it re...
- Q76. A container running a Python script is failing when it reaches the integration testing pha...
- Q77. Where should distributed load balancing occur in a horizontally scalable architecture?...
- Q78. Drag and drop the steps from the left into the order on the right to configure and install...
- Q79. What is a well-defined concept of GDPR compliance?...
- Q80. Drag and drop the REST API authentication method from the left to the description on the r...
- Q81. Drag and drop the expressions from below onto the code to implement error handling. Not al...
- Q82. Drag and Drop Question Drag and Drop the application requirement on the left onto the data...
- Q83. (Exhibit) Click on the Meraki Resources tab in the left corner to view Meraki documentatio...
- Q84. (Exhibit) Refer to the exhibit above and click on the tab in the top left corner to view a...
- Q85. Refer of the exhibit. Click on the resource labs in the top left corner to view resources ...
- Q86. A client is written that uses a REST API to interact with a server. Using HTTPS as the tra...
- Q87. Drag and drop the descriptions from the left onto the related OAuth-defined roles on the r...
- Q88. Refer to the exhibit. (Exhibit) A Python script has these requirements * Retrieve a list o...
- Q89. Refer to the exhibit. (Exhibit) Drag and drop the code from the bottom onto the box where ...
- Q90. A developer needs to configure an environment to orchestrate and configure. Which two tool...
- Q91. Drag and Drop the application requirement on the left onto the database type that should b...
- Q92. A developer has created an application based on customer requirements. The customer needs ...
- Q93. Drag and Drop Question Refer to the exhibit. Drag and drop the code snippets from the left...
- Q94. What is the result of a successful OAuth2 authorization grant flow?...
- Q95. Drag and Drop Question Drag and drop the git commands from the left into the correct order...
- Q96. A developer is creating a Python script to use the Webex Teams REST API to list joined spa...
- Q97. A local Docker container with a Container ID of 391441516e7a is running a Python applicati...
- Q98. Refer to the exhibit. (Exhibit) Two editors are concurrently updating an article's headlin...
- Q99. A developer has created an application based on customer requirements. The customer needs ...
- Q100. (Exhibit) Click on the GET Resource button above to view resources that will help with thi...
- Q101. Drag and drop the code from the bottom onto the box where the code is missing on the Ansib...
- Q102. Refer to the exhibit. (Exhibit) A developer must configure an SSL certificate for an nginx...
- Q103. An engineer needs to configure an interface named GigabitEthernet3 with an IP address on s...
- Q104. (Exhibit) Refer to the exhibit above and click on the tab in the top left corner to view a...
- Q105. Refer to the exhibit. (Exhibit) Drag and drop the code snippets from the left onto the ite...
- Q106. A developer needs to build a new Docker image and has created a tag by using the command: ...
- Q107. Refer to the exhibit. (Exhibit) Drag and drop the parts of the Python code from the left o...
- Q108. Drag and drop the steps from the left into the sequence on the fight to implement an OAuth...
- Q109. Refer to the exhibit. (Exhibit) A company has extended networking from the data center to ...
- Q110. Which RFC5988 (Web Linking) relation type is used in the Link header to control pagination...
- Q111. Drag and drop the REST API authentication method from the left to the description on the r...
- Q112. Drag and drop the code from the bottom onto the box where the code is missing in the Ansib...
- Q113. Refer to the exhibit. (Exhibit) This snippet of a script has recently started exiting abno...
- Q114. Which scenario is an example of the pseudonymization of sensitive data that meets GDPR req...
- Q115. Meraki Dashboard API Response Response Status Code200 Response Link Header <https://n6....
- Q116. An architect must optimize traffic that targets a popular API endpoint Currently, the appl...
- Q117. Refer to the exhibit. A system administrator has installed a Linux-based alarm system in t...
- Q118. When end-to-end encryption is implemented, which area is most vulnerable to exploitation?...
- Q119. Drag and drop the code snippets from the bottom onto.the boxes where the code is missing t...
- Q120. A developer must package an application for Kubernetes to integrate into a prebuilt CD env...
- Q121. A Python script must query the Cisco DNA center API for the number of unique wireless clie...
- Q122. Drag and drop the steps from the left into the sequence on the fight to implement an OAuth...
- Q123. A web application is susceptible to cross-site scripting. Which two methods allow this iss...
- Q124. Drag and drop the code from the bottom onto the box where the code is rrnssmg to create a ...
- Q125. Refer to the exhibit. (Exhibit) What is the output of this IOS-XE configuration program?...
- Q126. Refer to the exhibit. (Exhibit) A Python script must list network clients in the Cisco Mer...
- Q127. Refer to the exhibit. (Exhibit) An Intersight API is being used to query RackUnit resource...
- Q128. (Exhibit) Refer to the exhibit above and click on the IETF Routing tab in the top left cor...
- Q129. What are two advantages of using model-driven telemetry, such as gRPC, instead of traditio...
- Q130. Refer to the exhibit. (Exhibit) An application is being developed as an information reposi...
- Q131. Drag and drop the expressions from below onto the code to implement error handling. Not al...
- Q132. (Exhibit) Refer to the exhibit. Drag and drop parts of the URL from the left onto the item...
- Q133. A heterogeneous network of vendors and device types needs automating for better efficiency...
- Q134. Drag and drop the code from the bottom onto the box where the code is missing the snippet ...
- Q135. Drag and drop the code onto the snippet to update a SSID in Meraki using the Dashboard API...
- Q136. Refer to the exhibit. Drag and drop the steps from the left into the correct order of oper...
- Q137. (Exhibit) Refer to the exhibit above and click on the resource tabs in the top left corner...
- Q138. Refer to the exhibit. (Exhibit) Drag and drop the code snippets from the bottom onto the b...
- Q139. Drag and drop the code snippets from the bottom onto the boxes where the code is missing t...
- Q140. Which two statements are considered best practices according to the 12-factor app methodol...
- Q141. Refer to the exhibit. (Exhibit) Which set of API requests must be executed by a Webex Team...
- Q142. Drag and drop the code from the bottom onto the box where the code is missing to create a ...
- Q143. Refer to the exhibit. The JSON response is received from the Meraki location API. Which pa...
- Q144. Drag and drop the code from the bottom onto the box where the code is missing to enable an...
- Q145. The Meraki API URL https://api.meraki.com/api/v0/networks/123456789/ssids/2 has been store...
- Q146. Drag and drop the steps from the left into the order on the right to configure and install...
- Q147. DRAG DROP (Exhibit) Refer to the exhibit. A system administrator has installed a Linux-bas...
- Q148. Which snippet presents the correct API call to configure, secure, and enable an SSID using...
- Q149. Refer to the exhibit. (Exhibit) Cisco IOS XE switches are used across the entire network a...
- Q150. Drag and drop the git commands from the left into the correct order on the right to create...
- Q151. Refer to the exhibit. Which snippet creates a Webex Teams space and adds the users in the ...
- Q152. (Exhibit) Refer to the exhibit above and click on the resource tabs in the top left corner...
- Q153. Refer to the exhibit. (Exhibit) A network engineer created a simple Python Flask applicati...
- Q154. Drag and drop the steps from the left into the order on the right to create the workflow t...
- Q155. Drag and drop the steps on the left into the order on the right for an end-user to access ...
- Q156. Refer to the exhibit. (Exhibit) An application's REST API GET call is tested to the invent...
- Q157. Drag and drop the characteristics from the left onto the correct data processing technique...
- Q158. How is client code that consumes gRPC telemetry implemented, assuming that the preferred l...
- Q159. Refer to the exhibit. Which code snippet is required in the headers to successfully author...
- Q160. DRAG DROP (Exhibit) Refer to the exhibit. Drag and drop the steps from the left into the c...
- Q161. (Exhibit) Refer to the exhibit above and click on the resource tabs in the top left corner...
- Q162. DRAG DROP (Exhibit) Refer to the exhibit. A system administrator has installed a Linux-bas...
- Q163. Refer to the exhibit. (Exhibit) What is the missing step in deploying a Docker container t...
- Q164. Where should distributed load balancing occur in a horizontally scalable architecture?...
- Q165. (Exhibit) Refer to the exhibits. An interface named "GigabitEthernet2" has been configured...
- Q166. Drag and drop the operations from the left into the order on the right to create a web das...
- Q167. Drag and drop the REST API authentication method from the left to the description on the r...
- Q168. A developer is creating a Python script to analyze errors during REST API call operations....
- Q169. Refer to the exhibit. (Exhibit) Drag and drop the code snippets from the left onto the ite...
- Q170. (Exhibit) Refer to the exhibit. Drag and drop parts of the URL from the left onto the item...
- Q171. Refer to the exhibit. (Exhibit) Python threading allows a developer to have different part...
- Q172. Drag and Drop Question Drag and drop the code from the bottom onto the box where the code ...
- Q173. DRAG DROP (Exhibit) Refer to the exhibit above and click on the resource tabs in the top l...
- Q174. In the three-legged OAuth2 authorization workflow, which entity grants access to a protect...
- Q175. Refer to the exhibit. (Exhibit) The Python script is supposed to make an API call to Cisco...
- Q176. Refer to the exhibit. (Exhibit) What is the output of this IOS-XE configuration program?...
- Q177. Refer to the exhibit. (Exhibit) Which URL retrieves the errors in the GigabitEthernet 1 in...
- Q178. (Exhibit) Refer to the exhibit above and click on the resource tabs in the top left corner...
- Q179. What are two principles according to the build, release, run principle of the twelve-facto...
- Q180. Refer to the exhibit. (Exhibit) Which configuration of method and parameter retrieves the ...
- Q181. (Exhibit) Refer to the exhibit above and click on the resource tabs in the top left corner...
- Q182. What is a characteristic of event-driven architecture?...
- Q183. (Exhibit) Refer to the exhibit above and click on the resource tabs in the top left corner...
- Q184. Drag and drop the expressions from below onto the code to implement error handling. Not al...
- Q185. An automated solution is needed to configure VMs in numerous cloud provider environments t...
- Q186. Refer to the exhibit. (Exhibit) Drag and drop the steps from the left into the correct ord...
- Q187. Refer to the exhibit. (Exhibit) Drag and drop the steps from the left into the order of op...
- Q188. Which two actions must be taken when an observable microservice application is developed? ...
- Q189. (Exhibit) Refer to the exhibit above and click on the resource tabs in the top left corner...
- Q190. (Exhibit) Click on the GET Resource button above to view resources that will help with thi...
- Q191. Drag and drop the code from the bottom onto the box where the code is missing in the diagr...
- Q192. Refer to the exhibit. (Exhibit) Many faults have occurred in the ACI environment and a sam...
- Q193. A container running a Python script is failing when it reaches the integration testing pha...
- Q194. A web application is susceptible to cross-site scripting. Which two methods allow this iss...
- Q195. Refer to the exhibit. (Exhibit) A developer is creating a Python script by using Cisco DNA...
- Q196. Which snippet presents the correct API call to configure, secure, and enable an SSID using...
- Q197. Which tow actions must be taken when an observable microservice application is developed? ...
- Q198. Refer to the exhibit. (Exhibit) The Ansible playbook is using the netconf_module to config...
- Q199. Refer to the exhibit. (Exhibit) The Python script is supposed to make an API call to Cisco...
- Q200. (Exhibit) Drag and drop the code snippets from the left onto the item numbers on the right...


