Join the discussion
Question 1/86
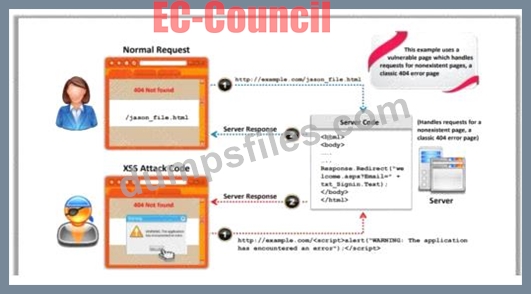
An attacker, in an attempt to exploit the vulnerability in the dynamically generated welcome page, inserted code at the end of the company's URL as follows:
http://technosoft.com.com/<script>alert("WARNING: The application has encountered an error");</script>.
Identify the attack demonstrated in the above scenario.
http://technosoft.com.com/<script>alert("WARNING: The application has encountered an error");</script>.
Identify the attack demonstrated in the above scenario.
Correct Answer: A
The attack demonstrated in the scenario is a Cross-site Scripting (XSS) attack. This is evident from the attacker's action of inserting a <script> tag into the URL, which is a common technique used in XSS attacks to execute malicious scripts in the context of the victim's browser. The script in the URL is designed to display an alert box with a warning message, which is a typical behavior of XSS to show that the attacker can execute JavaScript in the user's browser session.
References The answer can be verified through EC-Council's Certified SOC Analyst (CSA) course materials and study guides, which cover various types of cyber attacks, including XSS, and their characteristics.
References The answer can be verified through EC-Council's Certified SOC Analyst (CSA) course materials and study guides, which cover various types of cyber attacks, including XSS, and their characteristics.

Add Comments
- Other Question (86q)
- Q1. An attacker, in an attempt to exploit the vulnerability in the dynamically generated welco...
- Q2. Which encoding replaces unusual ASCII characters with "%" followed by the character's two-...
- Q3. Identify the type of attack, an attacker is attempting on www.example.com website. (Exhibi...
- Q4. According to the Risk Matrix table, what will be the risk level when the probability of an...
- Q5. John, a SOC analyst, while monitoring and analyzing Apache web server logs, identified an ...
- Q6. Which of the following attacks causes sudden changes in file extensions or increase in fil...
- Q7. The threat intelligence, which will help you, understand adversary intent and make informe...
- Q8. An attacker, in an attempt to exploit the vulnerability in the dynamically generated welco...
- Q9. Harley is working as a SOC analyst with Powell Tech. Powell Inc. is using Internet Informa...
- Q10. If the SIEM generates the following four alerts at the same time: I.Firewall blocking traf...
- Q11. Which attack works like a dictionary attack, but adds some numbers and symbols to the word...
- Q12. Which of the following data source can be used to detect the traffic associated with Bad B...
- Q13. John, a threat analyst at GreenTech Solutions, wants to gather information about specific ...
- Q14. Which of the following service provides phishing protection and content filtering to manag...
- Q15. Juliea a SOC analyst, while monitoring logs, noticed large TXT, NULL payloads. What does t...
- Q16. InfoSystem LLC, a US-based company, is establishing an in-house SOC. John has been given t...
- Q17. Identify the attack in which the attacker exploits a target system through publicly known ...
- Q18. Ray is a SOC analyst in a company named Queens Tech. One Day, Queens Tech is affected by a...
- Q19. Emmanuel is working as a SOC analyst in a company named Tobey Tech. The manager of Tobey T...
- Q20. Which of the following is a report writing tool that will help incident handlers to genera...
- Q21. Which of the following Windows features is used to enable Security Auditing in Windows?...
- Q22. Which of the following is a default directory in a Mac OS X that stores security-related l...
- Q23. Sam, a security analyst with INFOSOL INC., while monitoring and analyzing IIS logs, detect...
- Q24. Which of the following data source will a SOC Analyst use to monitor connections to the in...
- Q25. Which of the following threat intelligence helps cyber security professionals such as secu...
- Q26. Which of the following threat intelligence helps cyber security professionals such as secu...
- Q27. Which of the following command is used to enable logging in iptables?...
- Q28. Peter, a SOC analyst with Spade Systems, is monitoring and analyzing the router logs of th...
- Q29. Which of the following Windows event is logged every time when a user tries to access the ...
- Q30. Wesley is an incident handler in a company named Maddison Tech. One day, he was learning t...
- Q31. Which of the following framework describes the essential characteristics of an organizatio...
- Q32. What is the correct sequence of SOC Workflow?
- Q33. Which of the following attack can be eradicated by disabling of "allow_url_fopen and allow...
- Q34. Jony, a security analyst, while monitoring IIS logs, identified events shown in the figure...
- Q35. Daniel is a member of an IRT, which was started recently in a company named Mesh Tech. He ...
- Q36. Which of the following formula represents the risk?...
- Q37. The threat intelligence, which will help you, understand adversary intent and make informe...
- Q38. In which log collection mechanism, the system or application sends log records either on t...
- Q39. Juliea a SOC analyst, while monitoring logs, noticed large TXT, NULL payloads. What does t...
- Q40. Which of the following is a default directory in a Mac OS X that stores security-related l...
- Q41. Which of the following data source can be used to detect the traffic associated with Bad B...
- Q42. Identify the attack when an attacker by several trial and error can read the contents of a...
- Q43. Which of the following factors determine the choice of SIEM architecture?...
- Q44. Which of the following process refers to the discarding of the packets at the routing leve...
- Q45. According to the forensics investigation process, what is the next step carried out right ...
- Q46. Which of the following is a Threat Intelligence Platform?...
- Q47. Identify the HTTP status codes that represents the server error....
- Q48. Which of the following formula represents the risk levels?...
- Q49. Which of the following attack can be eradicated by disabling of "allow_url_fopen and allow...
- Q50. Emmanuel is working as a SOC analyst in a company named Tobey Tech. The manager of Tobey T...
- Q51. Which of the following formula is used to calculate the EPS of the organization?...
- Q52. Which of the following is a set of standard guidelines for ongoing development, enhancemen...
- Q53. Which of the following tool can be used to filter web requests associated with the SQL Inj...
- Q54. What is the process of monitoring and capturing all data packets passing through a given n...
- Q55. Which of the following steps of incident handling and response process focus on limiting t...
- Q56. Which of the following Windows Event Id will help you monitors file sharing across the net...
- Q57. Harley is working as a SOC analyst with Powell Tech. Powell Inc. is using Internet Informa...
- Q58. John, SOC analyst wants to monitor the attempt of process creation activities from any of ...
- Q59. Which of the following Windows event is logged every time when a user tries to access the ...
- Q60. Identify the attack, where an attacker tries to discover all the possible information abou...
- Q61. Which of the following technique protects from flooding attacks originated from the valid ...
- Q62. Which of the following is a set of standard guidelines for ongoing development, enhancemen...
- Q63. Jane, a security analyst, while analyzing IDS logs, detected an event matching Regex /((\%...
- Q64. Which of the following fields in Windows logs defines the type of event occurred, such as ...
- Q65. Which of the following technique involves scanning the headers of IP packets leaving a net...
- Q66. John as a SOC analyst is worried about the amount of Tor traffic hitting the network. He w...
- Q67. Which of the following tool is used to recover from web application incident?...
- Q68. Which of the following is a default directory in a Mac OS X that stores security-related l...
- Q69. Bonney's system has been compromised by a gruesome malware. What is the primary step that ...
- Q70. Identify the HTTP status codes that represents the server error....
- Q71. Daniel is a member of an IRT, which was started recently in a company named Mesh Tech. He ...
- Q72. A type of threat intelligent that find out the information about the attacker by misleadin...
- Q73. An attacker exploits the logic validation mechanisms of an e-commerce website. He successf...
- Q74. Jason, a SOC Analyst with Maximus Tech, was investigating Cisco ASA Firewall logs and came...
- Q75. Which of the following are the responsibilities of SIEM Agents? 1.Collecting data received...
- Q76. According to the Risk Matrix table, what will be the risk level when the probability of an...
- Q77. Charline is working as an L2 SOC Analyst. One day, an L1 SOC Analyst escalated an incident...
- Q78. Rinni, SOC analyst, while monitoring IDS logs detected events shown in the figure below. (...
- Q79. Which of the following factors determine the choice of SIEM architecture?...
- Q80. Emmanuel is working as a SOC analyst in a company named Tobey Tech. The manager of Tobey T...
- Q81. Which of the following is a report writing tool that will help incident handlers to genera...
- Q82. Which of the following stage executed after identifying the required event sources?...
- Q83. Which of the following formula represents the risk levels?...
- Q84. Which of the log storage method arranges event logs in the form of a circular buffer?...
- Q85. Which of the following is a Threat Intelligence Platform?...
- Q86. Charline is working as an L2 SOC Analyst. One day, an L1 SOC Analyst escalated an incident...


