Join the discussion
Question 1/112
Harry. a professional hacker, targets the IT infrastructure of an organization. After preparing for the attack, he attempts to enter the target network using techniques such as sending spear-phishing emails and exploiting vulnerabilities on publicly available servers. Using these techniques, he successfully deployed malware on the target system to establish an outbound connection. What is the APT lifecycle phase that Harry is currently executing?
Correct Answer: A
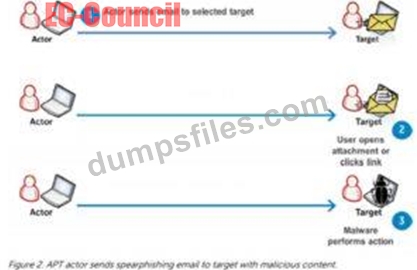
After the attacker completes preparations, subsequent step is an effort to realize an edge within the target's environment. a particularly common entry tactic is that the use of spearphishing emails containing an internet link or attachment. Email links usually cause sites where the target's browser and related software are subjected to varied exploit techniques or where the APT actors plan to social engineer information from the victim which will be used later. If a successful exploit takes place, it installs an initial malware payload on the victim's computer. Figure 2 illustrates an example of a spearphishing email that contains an attachment. Attachments are usually executable malware, a zipper or other archive containing malware, or a malicious Office or Adobe PDF (Portable Document Format) document that exploits vulnerabilities within the victim's applications to ultimately execute malware on the victim's computer. Once the user has opened a malicious file using vulnerable software, malware is executing on the target system. These phishing emails are often very convincing and difficult to differentiate from legitimate email messages. Tactics to extend their believability include modifying legitimate documents from or associated with the organization. Documents are sometimes stolen from the organization or their collaborators during previous exploitation operations. Actors modify the documents by adding exploits and malicious code then send them to the victims. Phishing emails are commonly sent through previously compromised email servers, email accounts at organizations associated with the target or public email services. Emails also can be sent through mail relays with modified email headers to form the messages appear to possess originated from legitimate sources. Exploitation of vulnerabilities on public-facing servers is another favorite technique of some APT groups. Though this will be accomplished using exploits for known vulnerabilities, 0-days are often developed or purchased to be used in intrusions as required .

Add Comments
- Other Question (112q)
- Q1. Harry. a professional hacker, targets the IT infrastructure of an organization. After prep...
- Q2. The Payment Card Industry Data Security Standard (PCI DSS) contains six different categori...
- Q3. ViruXine.W32 virus hides their presence by changing the underlying executable code. This V...
- Q4. When analyzing the IDS logs, the system administrator noticed an alert was logged when the...
- Q5. Joseph was the Web site administrator for the Mason Insurance in New York, who's main Web ...
- Q6. An attacker scans a host with the below command. Which three flags are set? # nmap -sX hos...
- Q7. Morris, a professional hacker, performed a vulnerability scan on a target organization by ...
- Q8. While using your bank's online servicing you notice the following string in the URL bar: "...
- Q9. What is the following command used for? sqlmap.py-u ,,http://10.10.1.20/?p=1&forumacti...
- Q10. What is one of the advantages of using both symmetric and asymmetric cryptography in SSL/T...
- Q11. Attempting an injection attack on a web server based on responses to True/False Question:s...
- Q12. Which results will be returned with the following Google search query? site:target.com - s...
- Q13. Websites and web portals that provide web services commonly use the Simple Object Access P...
- Q14. On performing a risk assessment, you need to determine the potential impacts when some of ...
- Q15. Nedved is an IT Security Manager of a bank in his country. One day. he found out that ther...
- Q16. An attacker identified that a user and an access point are both compatible with WPA2 and W...
- Q17. You are using a public Wi-Fi network inside a coffee shop. Before surfing the web, you use...
- Q18. Which of the following Bluetooth hacking techniques does an attacker use to send messages ...
- Q19. Shellshock allowed an unauthorized user to gain access to a server. It affected many Inter...
- Q20. which of the following Bluetooth hacking techniques refers to the theft of information fro...
- Q21. Gregory, a professional penetration tester working at Sys Security Ltd., is tasked with pe...
- Q22. Mirai malware targets loT devices. After infiltration, it uses them to propagate and creat...
- Q23. Eve is spending her day scanning the library computers. She notices that Alice is using a ...
- Q24. You have compromised a server and successfully gained a root access. You want to pivot and...
- Q25. While scanning with Nmap, Patin found several hosts which have the IP ID of incremental se...
- Q26. A user on your Windows 2000 network has discovered that he can use L0phtcrack to sniff the...
- Q27. Which of the following types of SQL injection attacks extends the results returned by the ...
- Q28. You have successfully comprised a server having an IP address of 10.10.0.5. You would like...
- Q29. Log monitoring tools performing behavioral analysis have alerted several suspicious logins...
- Q30. John wants to send Marie an email that includes sensitive information, and he does not tru...
- Q31. Alice needs to send a confidential document to her coworker. Bryan. Their company has publ...
- Q32. An Internet Service Provider (ISP) has a need to authenticate users connecting via analog ...
- Q33. Your company was hired by a small healthcare provider to perform a technical assessment on...
- Q34. A network administrator discovers several unknown files in the root directory of his Linux...
- Q35. Suppose your company has just passed a security risk assessment exercise. The results disp...
- Q36. The security team of Debry Inc. decided to upgrade Wi-Fi security to thwart attacks such a...
- Q37. A post-breach forensic investigation revealed that a known vulnerability in Apache Struts ...
- Q38. When considering how an attacker may exploit a web server, what is web server footprinting...
- Q39. You need a tool that can do network intrusion prevention and intrusion detection, function...
- Q40. You have the SOA presented below in your Zone. Your secondary servers have not been able t...
- Q41. Which wireless security protocol replaces the personal pre-shared key (PSK) authentication...
- Q42. Robin, an attacker, is attempting to bypass the firewalls of an organization through the D...
- Q43. Bill is a network administrator. He wants to eliminate unencrypted traffic inside his comp...
- Q44. Ethical backer jane Doe is attempting to crack the password of the head of the it departme...
- Q45. Robert, a professional hacker, is attempting to execute a fault injection attack on a targ...
- Q46. Widespread fraud ac Enron. WorldCom, and Tyco led to the creation of a law that was design...
- Q47. Study the snort rule given below: (Exhibit) From the options below, choose the exploit aga...
- Q48. The network users are complaining because their system are slowing down. Further, every ti...
- Q49. You work for Acme Corporation as Sales Manager. The company has tight network security res...
- Q50. In this attack, a victim receives an e-mail claiming from PayPal stating that their accoun...
- Q51. An organization is performing a vulnerability assessment tor mitigating threats. James, a ...
- Q52. Harris is attempting to identify the OS running on his target machine. He inspected the in...
- Q53. What useful information is gathered during a successful Simple Mail Transfer Protocol (SMT...
- Q54. Which of the following scanning method splits the TCP header into several packets and make...
- Q55. David is a security professional working in an organization, and he is implementing a vuln...
- Q56. What is the BEST alternative if you discover that a rootkit has been installed on one of y...
- Q57. When conducting a penetration test, it is crucial to use all means to get all available in...
- Q58. The change of a hard drive failure is once every three years. The cost to buy a new hard d...
- Q59. You just set up a security system in your network. In what kind of system would you find t...
- Q60. You want to do an ICMP scan on a remote computer using hping2. What is the proper syntax?...
- Q61. Samuel a security administrator, is assessing the configuration of a web server. He notice...
- Q62. What two conditions must a digital signature meet?...
- Q63. BitLocker encryption has been implemented for all the Windows-based computers in an organi...
- Q64. Identify the correct terminology that defines the above statement....
- Q65. ViruXine.W32 virus hides their presence by changing the underlying executable code. This V...
- Q66. George, an employee of an organization, is attempting to access restricted websites from a...
- Q67. Firewalls are the software or hardware systems that are able to control and monitor the tr...
- Q68. John, a professional hacker, decided to use DNS to perform data exfiltration on a target n...
- Q69. What kind of detection techniques is being used in antivirus software that identifies malw...
- Q70. Abel, a cloud architect, uses container technology to deploy applications/software includi...
- Q71. Jude, a pen tester, examined a network from a hacker's perspective to identify exploits an...
- Q72. Which of the following programs is usually targeted at Microsoft Office products?...
- Q73. What does the following command in netcat do? nc -l -u -p55555 < /etc/passwd...
- Q74. Which of the following allows attackers to draw a map or outline the target organization's...
- Q75. Which of the following is not a Bluetooth attack?...
- Q76. In both pharming and phishing attacks, an attacker can create websites that look similar t...
- Q77. Based on the following extract from the log of a compromised machine, what is the hacker r...
- Q78. Which type of sniffing technique is generally referred as MiTM attack? (Exhibit)...
- Q79. #!/usr/bin/python import socket buffer=[""A""] counter=50 while len(buffer)<=100: buffe...
- Q80. A bank stores and processes sensitive privacy information related to home loans. However, ...
- Q81. Becky has been hired by a client from Dubai to perform a penetration test against one of t...
- Q82. Which of these is capable of searching for and locating rogue access points?...
- Q83. Which of the following is the primary objective of a rootkit?...
- Q84. Which DNS resource record can indicate how long any "DNS poisoning" could last?...
- Q85. Johnson, an attacker, performed online research for the contact details of reputed cyberse...
- Q86. Which command can be used to show the current TCP/IP connections?...
- Q87. Which utility will tell you in real time which ports are listening or in another state?...
- Q88. To invisibly maintain access to a machine, an attacker utilizes a toolkit that sits undete...
- Q89. Study the snort rule given below and interpret the rule. alert tcp any any --> 192.168....
- Q90. E-mail scams and mail fraud are regulated by which of the following?...
- Q91. Which among the following is the best example of the third step (delivery) in the cyber ki...
- Q92. From the following table, identify the wrong answer in terms of Range (ft). Standard Range...
- Q93. Peter, a Network Administrator, has come to you looking for advice on a tool that would he...
- Q94. Which file is a rich target to discover the structure of a website during web-server footp...
- Q95. Ben purchased a new smartphone and received some updates on it through the OTA method. He ...
- Q96. You have retrieved the raw hash values from a Windows 2000 Domain Controller. Using social...
- Q97. You went to great lengths to install all the necessary technologies to prevent hacking att...
- Q98. A hacker has successfully infected an internet-facing server which he will then use to sen...
- Q99. While performing an Nmap scan against a host, Paola determines the existence of a firewall...
- Q100. Emily, an extrovert obsessed with social media, posts a large amount of private informatio...
- Q101. Bob, a system administrator at TPNQM SA, concluded one day that a DMZ is not needed if he ...
- Q102. What is the algorithm used by LM for Windows2000 SAM?...
- Q103. Suppose that you test an application for the SQL injection vulnerability. You know that th...
- Q104. SQL injection (SQLi) attacks attempt to inject SQL syntax into web requests, which may Byp...
- Q105. Which access control mechanism allows for multiple systems to use a central authentication...
- Q106. Which method of password cracking takes the most time and effort?...
- Q107. During the enumeration phase. Lawrence performs banner grabbing to obtain information such...
- Q108. What is the following command used for? net use \targetipc$ "" /u:""...
- Q109. The tools which receive event logs from servers, network equipment, and applications, and ...
- Q110. Tony is a penetration tester tasked with performing a penetration test. After gaining init...
- Q111. You are trying to break into a highly classified top-secret mainframe computer with highes...
- Q112. John, a disgruntled ex-employee of an organization, contacted a professional hacker to exp...


