Join the discussion
Question 1/11
Refer to the exhibits.
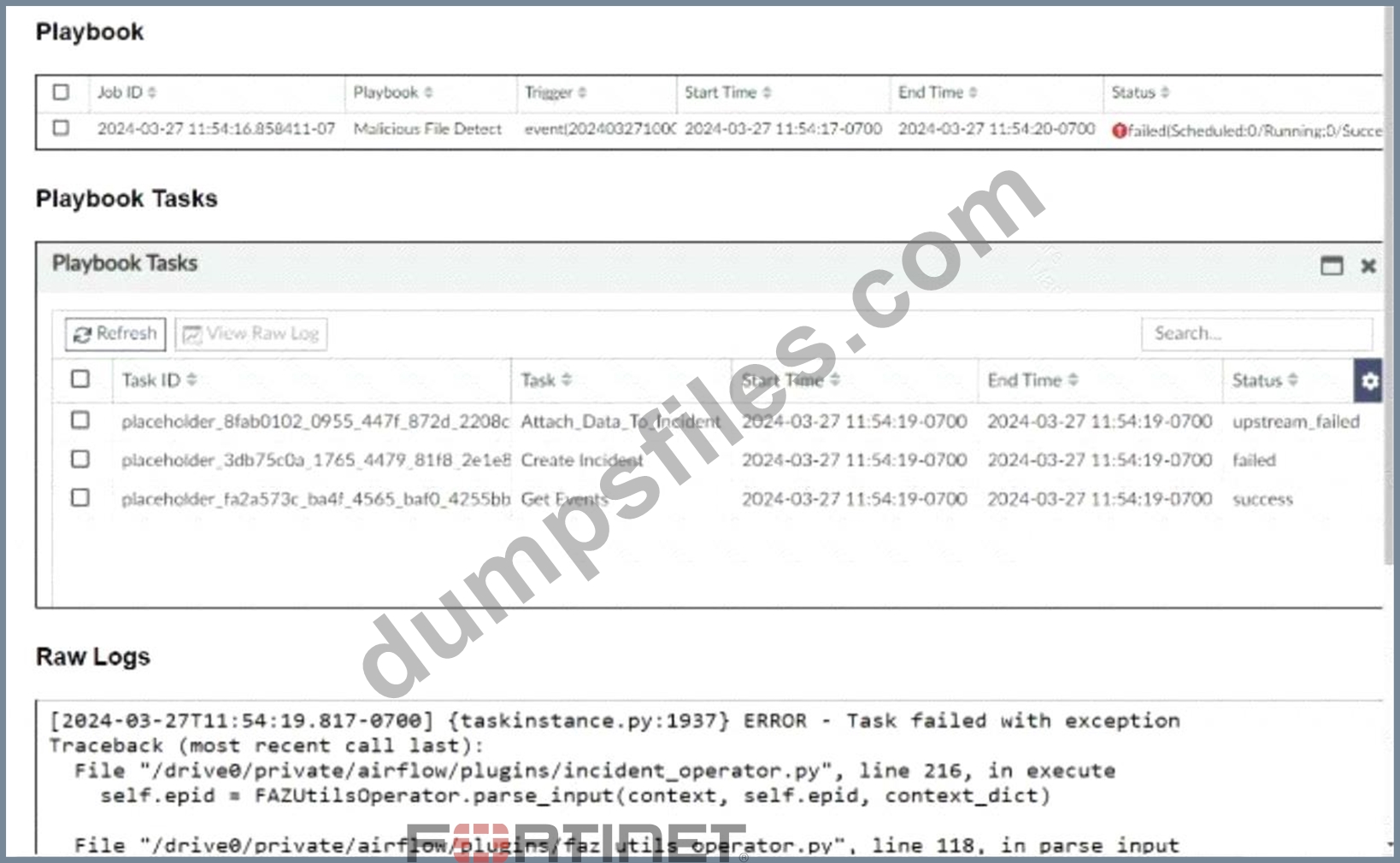
The Malicious File Detect playbook is configured to create an incident when an event handler generates a malicious file detection event.
Why did the Malicious File Detect playbook execution fail?

The Malicious File Detect playbook is configured to create an incident when an event handler generates a malicious file detection event.
Why did the Malicious File Detect playbook execution fail?
Correct Answer: A
* Understanding the Playbook Configuration:
* The "Malicious File Detect" playbook is designed to create an incident when a malicious file detection event is triggered.
* The playbook includes tasks such asAttach_Data_To_Incident,Create Incident, andGet Events.
* Analyzing the Playbook Execution:
* The exhibit shows that theCreate Incidenttask has failed, and theAttach_Data_To_Incidenttask has also failed.
* TheGet Eventstask succeeded, indicating that it was able to retrieve event data.
* Reviewing Raw Logs:
* The raw logs indicate an error related to parsing input in theincident_operator.pyfile.
* The error traceback suggests that the task was expecting a specific input format (likely a name or number) but received an incorrect data format.
* Identifying the Source of the Failure:
* TheCreate Incidenttask failure is the root cause since it did not proceed correctly due to incorrect input format.
* TheAttach_Data_To_Incidenttask subsequently failed because it depends on the successful creation of an incident.
* Conclusion:
* The primary reason for the playbook execution failure is that theCreate Incidenttask received an incorrect data format, which was not a name or number as expected.
References:
* Fortinet Documentation on Playbook and Task Configuration.
* Error handling and debugging practices in playbook execution.
* The "Malicious File Detect" playbook is designed to create an incident when a malicious file detection event is triggered.
* The playbook includes tasks such asAttach_Data_To_Incident,Create Incident, andGet Events.
* Analyzing the Playbook Execution:
* The exhibit shows that theCreate Incidenttask has failed, and theAttach_Data_To_Incidenttask has also failed.
* TheGet Eventstask succeeded, indicating that it was able to retrieve event data.
* Reviewing Raw Logs:
* The raw logs indicate an error related to parsing input in theincident_operator.pyfile.
* The error traceback suggests that the task was expecting a specific input format (likely a name or number) but received an incorrect data format.
* Identifying the Source of the Failure:
* TheCreate Incidenttask failure is the root cause since it did not proceed correctly due to incorrect input format.
* TheAttach_Data_To_Incidenttask subsequently failed because it depends on the successful creation of an incident.
* Conclusion:
* The primary reason for the playbook execution failure is that theCreate Incidenttask received an incorrect data format, which was not a name or number as expected.
References:
* Fortinet Documentation on Playbook and Task Configuration.
* Error handling and debugging practices in playbook execution.
Add Comments
- Other Question (11q)
- Q1. Refer to the exhibits. (Exhibit) The Malicious File Detect playbook is configured to creat...
- Q2. Refer to Exhibit: (Exhibit) You are tasked with reviewing a new FortiAnalyzer deployment i...
- Q3. While monitoring your network, you discover that one FortiGate device is sending significa...
- Q4. When configuring a FortiAnalyzer to act as a collector device, which two steps must you pe...
- Q5. Review the following incident report: Attackers leveraged a phishing email campaign target...
- Q6. Refer to the exhibit. (Exhibit) Assume that all devices in the FortiAnalyzer Fabric are sh...
- Q7. A customer wants FortiAnalyzer to run an automation stitch that executes a CLI command on ...
- Q8. Refer to the exhibits. (Exhibit) The FortiMail Sender Blocklist playbook is configured to ...
- Q9. When configuring a FortiAnalyzer to act as a collector device, which two steps must you pe...
- Q10. Refer to the exhibits. (Exhibit) You configured a custom event handler and an associated r...
- Q11. Refer to the Exhibit: (Exhibit) An analyst wants to create an incident and generate a repo...

[×]
Download PDF File
Enter your email address to download Fortinet.FCSS_SOC_AN-7.4.v2024-10-22.q11.pdf

