Join the discussion
Question 1/122
You work as a Network Administrator for Net World International. You have configured the hard disk drive of your computer as shown in the image below:
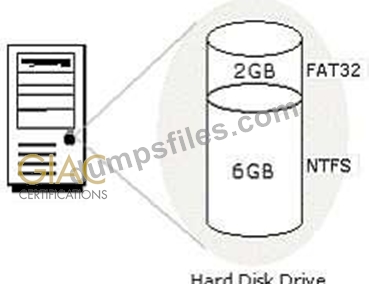
The computer is configured to dual-boot with Windows 2000 Server and Windows 98. While working on Windows 2000 Server, you save a file on the 6GB partition. You are unable to find the file while working on Windows 98. You are not even able to access the partition on which the file is saved. What is the most likely cause?

The computer is configured to dual-boot with Windows 2000 Server and Windows 98. While working on Windows 2000 Server, you save a file on the 6GB partition. You are unable to find the file while working on Windows 98. You are not even able to access the partition on which the file is saved. What is the most likely cause?
Correct Answer: C
Section: Volume A
Add Comments
- Other Question (122q)
- Q1. You work as a Network Administrator for Net World International. You have configured the h...
- Q2. John works as a professional Ethical Hacker. He has been assigned the project of testing t...
- Q3. You work as a Network Administrator for Perfect Solutions Inc. You have to install Windows...
- Q4. John works as a contract Ethical Hacker. He has recently got a project to do security chec...
- Q5. Adam works as a professional Computer Hacking Forensic Investigator. A project has been as...
- Q6. Which of the following firewalls depends on the three-way handshake of the TCP protocol?...
- Q7. Which of the following enables an inventor to legally enforce his right to exclude others ...
- Q8. Adam works as a Computer Hacking Forensic Investigator. He has been assigned a project to ...
- Q9. Which of the following Acts enacted in United States amends Civil Rights Act of 1964, prov...
- Q10. This type of virus infects programs that can execute and load into memory to perform prede...
- Q11. Which of the following provides high availability of data?...
- Q12. You are responsible for maintaining and troubleshooting PC's at your company. The receptio...
- Q13. Victor works as a professional Ethical Hacker for SecureEnet Inc. He has been assigned a j...
- Q14. You are a professional Computer Hacking forensic investigator. You have been called to col...
- Q15. Which of the following tools are used to determine the hop counts of an IP packet? Each co...
- Q16. Which of the following are the primary goals of the incident handling team? Each correct a...
- Q17. Which of the following Acts enacted in United States allows the FBI to issue National Secu...
- Q18. Which of the following is the first computer virus that was used to infect the boot sector...
- Q19. Adam works as a Computer Hacking Forensic Investigator in a law firm. He has been assigned...
- Q20. An attacker attempts to gain information about a network by specifically targeting the net...
- Q21. The MBR of a hard disk is a collection of boot records that contain disk information such ...
- Q22. Which of the following precautionary steps are taken by the supervisors or employers to av...
- Q23. Sandra, a novice computer user, works on Windows environment. She experiences some problem...
- Q24. Which of the following is used to back up forensic evidences or data folders from the netw...
- Q25. Adam works as a professional Computer Hacking Forensic Investigator. A project has been as...
- Q26. In the United States, Title VII of the 1964 Civil Rights Act was formulated to protect an ...
- Q27. Which of the following terms refers to a mechanism which proves that the sender really sen...
- Q28. Peter, an expert computer user, attached a new sound card to his computer. He then restart...
- Q29. In a Windows 98 computer, which of the following utilities is used to convert a FAT16 part...
- Q30. John works as a professional Ethical Hacker. He has been assigned a project to test the se...
- Q31. Which of the following switches of the XCOPY command copies file ownerships and NTFS permi...
- Q32. Adam works as a Security Analyst for Umbrella Inc. He suspects that a virus exists in the ...
- Q33. On which of the following locations does the Windows NT/2000 operating system contain the ...
- Q34. John works as a professional Ethical Hacker. He has been assigned the project of testing t...
- Q35. Which of the following standard file formats is used by Apple's iPod to store contact info...
- Q36. You work as the Network Administrator for McNeil Inc. The company has a Unix-based network...
- Q37. TCP FIN scanning is a type of stealth scanning through which the attacker sends a FIN pack...
- Q38. Victor works as a professional Ethical Hacker for SecureEnet Inc. He has been assigned a j...
- Q39. Which of the following is a password-cracking program?...
- Q40. Adrian, the Network Administrator for Peach Tree Inc., wants to install a new computer on ...
- Q41. Adam, a malicious hacker, hides a hacking tool from a system administrator of his company ...
- Q42. Which of the following tools is a wireless sniffer and analyzer that works on the Windows ...
- Q43. Which of the following commands is used to create or delete partitions on Windows XP?...
- Q44. You work as a Network Administrator for Perfect Solutions Inc. You install Windows 98 on a...
- Q45. You are a professional Computer Hacking forensic investigator. You have been called to col...
- Q46. Which of the following is the Windows feature on which the file management can be performe...
- Q47. Which of the following tools in Helix Windows Live is used to reveal the database password...
- Q48. Adam works as a professional Computer Hacking Forensic Investigator. He has been assigned ...
- Q49. Which of the following is a file management tool?...
- Q50. You work as a Network Administrator for Net Perfect Inc. The company has a Windows Server ...
- Q51. Adam works as a Computer Hacking Forensic Investigator in a law firm. He has been assigned...
- Q52. On your dual booting computer, you want to set Windows 98 as the default operating system ...
- Q53. Which of the following switches is used with Pslist command on the command line to show th...
- Q54. You are the Network Administrator and your company has recently implemented encryption for...
- Q55. You are the Security Consultant and have been contacted by a client regarding their encryp...
- Q56. Which of the following is used for remote file access by UNIX/Linux systems?...
- Q57. Which of the following is NOT an example of passive footprinting?...
- Q58. Which of the following is described in the following statement? "It is a 512 bytes long bo...
- Q59. Which of the following statements about an extended partition are true? Each correct answe...
- Q60. You work as a Network Administrator for Net World International. You want to configure a W...
- Q61. Which of the following is a correct sequence of different layers of Open System Interconne...
- Q62. Nathan works as a professional Ethical Hacker. He wants to see all open TCP/IP and UDP por...
- Q63. Peter works as a Computer Hacking Forensic Investigator for SecureEnet Inc. He has been as...
- Q64. The MBR of a hard disk is a collection of boot records that contain disk information such ...
- Q65. Sam works as a professional Computer Hacking Forensic Investigator. A project has been ass...
- Q66. Adam works as a professional Computer Hacking Forensic Investigator. A project has been as...
- Q67. A customer comes to you stating that his hard drive has crashed. He had backed up the hard...
- Q68. Adam works as a professional Computer Hacking Forensic Investigator, a project has been as...
- Q69. Which of the following describes software technologies that improve portability, manageabi...
- Q70. Sam works as a professional Computer Hacking Forensic Investigator. A project has been ass...
- Q71. You are the Security Consultant and have been hired to check security for a client's netwo...
- Q72. Allen works as a professional Computer Hacking Forensic Investigator. A project has been a...
- Q73. Which of the following hardware devices prevents broadcasts from crossing over subnets?...
- Q74. You are reviewing a Service Level Agreement between your company and a Web development ven...
- Q75. Adam works as a professional Computer Hacking Forensic Investigator. He has been assigned ...
- Q76. Which of the following tools are used to determine the hop counts of an IP packet? Each co...
- Q77. John works as a Technical Support Executive in ABC Inc. The company's network consists of ...
- Q78. Sandra, an expert computer user, hears five beeps while booting her computer that has AMI ...
- Q79. John works as a contract Ethical Hacker. He has recently got a project to do security chec...
- Q80. Which of the following is the correct order of loading system files into the main memory o...
- Q81. You work as a Network Administrator for Perfect Solutions Inc. You have to install Windows...
- Q82. Which of the following is described in the following statement? "It is a 512 bytes long bo...
- Q83. You work as a Network Administrator for Net World International. Rick, a Sales Manager, co...
- Q84. Which of the following Windows Registry key contains the password file of the user?...
- Q85. Your network has a Windows 2000 Server computer with FAT file system, shared by several us...
- Q86. You work as a Computer Hacking Forensic Investigator for SecureNet Inc. You want to invest...
- Q87. Which of the following is the correct order of loading system files into the main memory o...
- Q88. Which of the following Linux file systems is a journaled file system?...
- Q89. Which of the following modules of OS X kernel (XNU) provides the primary system program in...
- Q90. Which of the following Incident handling process phases is responsible for defining rules,...
- Q91. Which of the following are the two different file formats in which Microsoft Outlook saves...
- Q92. Which of the following statements is NOT true about FAT16 file system? Each correct answer...
- Q93. You work as a Network Administrator for McNeel Inc. You want to encrypt each user's MY DOC...
- Q94. Which of the following is used to store configuration settings and options on Microsoft Wi...
- Q95. Which of the following commands can you use to create an ext3 file system? Each correct an...
- Q96. Which of the following sections of an investigative report covers the background and summa...
- Q97. You are handling technical support calls for an insurance company. A user calls you compla...
- Q98. You work as a Web developer for ABC Inc. You want to investigate the Cross-Site Scripting ...
- Q99. You work as a Network Administrator for Peach Tree Inc. The company currently has a FAT-ba...
- Q100. You work as a Network Security Analyzer. You got a suspicious email while working on a for...
- Q101. John works as a professional Ethical Hacker. He has been assigned the project of testing t...
- Q102. Which of the following commands is used to enforce checking of a file system even if the f...
- Q103. Which of the following needs to be documented to preserve evidences for presentation in co...
- Q104. Which of the following types of virus makes changes to a file system of a disk?...
- Q105. Peter, an expert computer user, attached a new sound card to his computer. He then restart...
- Q106. Which of the following tools is a wireless sniffer and analyzer that works on the Windows ...
- Q107. Which of the following laws enacted in United States makes it illegal for an Internet Serv...
- Q108. Adam works as a professional Computer Hacking Forensic Investigator with the local police ...
- Q109. Adam, a malicious hacker, hides a hacking tool from a system administrator of his company ...
- Q110. Your network has a Windows 2000 Server computer with FAT file system, shared by several us...
- Q111. You use the FAT16 file system on your Windows 98 computer. You want to upgrade to the FAT3...
- Q112. Which of the following laws or acts, formed in Australia, enforces prohibition against cyb...
- Q113. You company suspects an employee of sending unauthorized emails to competitors. These emai...
- Q114. Mark is the Administrator of a Linux computer. He wants to check the status of failed Teln...
- Q115. John used to work as a Network Administrator for We-are-secure Inc. Now he has resigned fr...
- Q116. Which of the following hardware devices prevents broadcasts from crossing over subnets?...
- Q117. Every network device contains a unique built in Media Access Control (MAC) address, which ...
- Q118. Which of the following commands is used to enforce checking of a file system even if the f...
- Q119. Which of the following is a nonvolatile form of memory that can be reprogrammed by using a...
- Q120. You work as a Network Administrator for Perfect Solutions Inc. The company has a Linux-bas...
- Q121. Joseph works as a Web Designer for WebTech Inc. He creates a Web site and wants to protect...
- Q122. Which of the following needs to be documented to preserve evidences for presentation in co...


