Join the discussion
Question 1/76
Exhibit:
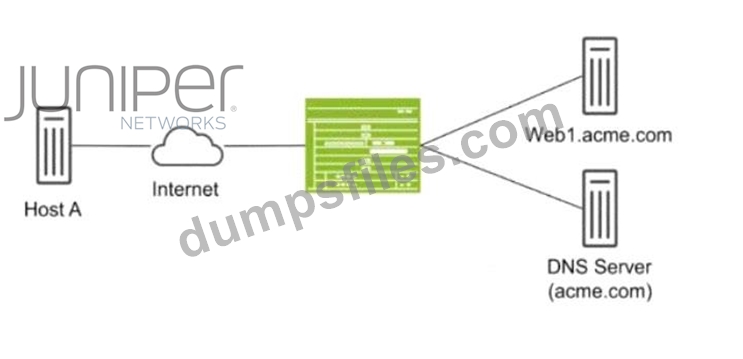
Host A shown in the exhibit is attempting to reach the Web1 webserver, but the connection is failing.
Troubleshooting reveals that when Host A attempts to resolve the domain name of the server (web.acme.
com), the request is resolved to the private address of the server rather than its public IP.
Which feature would you configure on the SRX Series device to solve this issue?

Host A shown in the exhibit is attempting to reach the Web1 webserver, but the connection is failing.
Troubleshooting reveals that when Host A attempts to resolve the domain name of the server (web.acme.
com), the request is resolved to the private address of the server rather than its public IP.
Which feature would you configure on the SRX Series device to solve this issue?
Correct Answer: C
DNS doctoring modifies DNS responses for hosts behind NAT devices, allowing them to receive the correct public IP address for internal resources when queried from the public network. This prevents issues where private IPs are returned and are not reachable externally. For details, visit Juniper DNS Doctoring Documentation.
In this scenario, Host A is trying to resolve the domain nameweb.acme.com, but the DNS resolution returns the private IP address of the web server instead of its public IP. This is a common issue in networks where private addresses are used internally, but public addresses are required for external clients.
* Explanation of Answer C (DNS Doctoring):
* DNS doctoringis a feature that modifies DNS replies as they pass through the SRX device. In this case, DNS doctoring can be used to replace the private IP address returned in the DNS response with the correct public IP address for Host A. This allows external clients to reach internal resources without being aware of their private IP addresses.
Configuration Example:
bash
Copy code
set security nat dns-doctoring from-zone untrust to-zone trust
Juniper Security Reference:
* DNS Doctoring Overview: DNS doctoring is used to modify DNS responses so that external clients can access internal resources using public IP addresses. Reference: Juniper DNS Doctoring Documentation.
In this scenario, Host A is trying to resolve the domain nameweb.acme.com, but the DNS resolution returns the private IP address of the web server instead of its public IP. This is a common issue in networks where private addresses are used internally, but public addresses are required for external clients.
* Explanation of Answer C (DNS Doctoring):
* DNS doctoringis a feature that modifies DNS replies as they pass through the SRX device. In this case, DNS doctoring can be used to replace the private IP address returned in the DNS response with the correct public IP address for Host A. This allows external clients to reach internal resources without being aware of their private IP addresses.
Configuration Example:
bash
Copy code
set security nat dns-doctoring from-zone untrust to-zone trust
Juniper Security Reference:
* DNS Doctoring Overview: DNS doctoring is used to modify DNS responses so that external clients can access internal resources using public IP addresses. Reference: Juniper DNS Doctoring Documentation.
Add Comments
- Other Question (76q)
- Q1. Exhibit: (Exhibit) Host A shown in the exhibit is attempting to reach the Web1 webserver, ...
- Q2. Exhibit (Exhibit) Your company recently acquired a competitor. You want to use using the s...
- Q3. What are three core components for enabling advanced policy-based routing? (Choose three.)...
- Q4. What are two valid modes for the Juniper ATP Appliance? (Choose two.)...
- Q5. You want to identify potential threats within SSL-encrypted sessions without requiring SSL...
- Q6. Exhibit: (Exhibit) You are configuring NAT64 on your SRX Series device. You have committed...
- Q7. Exhibit (Exhibit) Referring to the exhibit, which two statements are true? (Choose two.)...
- Q8. You have deployed automated threat mitigation using Security Director with Policy Enforcer...
- Q9. You are deploying a large-scale VPN spanning six sites. You need to choose a VPN technolog...
- Q10. You are using trace options to troubleshoot a security policy on your SRX Series device. (...
- Q11. Exhibit (Exhibit) The show network-access aaa radius-servers command has been issued to so...
- Q12. Exhibit (Exhibit) Referring to the exhibit, which type of NAT is being performed?...
- Q13. Which three type of peer devices are supported for Cos-Based IPsec VPN?...
- Q14. The exhibit shows part of the flow session logs. (Exhibit) Which two statements are true i...
- Q15. You want to enforce I DP policies on HTTP traffic. In this scenario, which two actions mus...
- Q16. You have a webserver and a DNS server residing in the same internal DMZ subnet. The public...
- Q17. you must find an infected host and where the aack came from using the Juniper ATP Cloud. W...
- Q18. You are asked to look at a configuration that is designed to take all traffic with a speci...
- Q19. You are configuring transparent mode on an SRX Series device. You must permit IP-based tra...
- Q20. Exhibit: (Exhibit) Referring to the exhibit, what do you use to dynamically secure traffic...
- Q21. Exhibit (Exhibit) You are implementing filter-based forwarding to send traffic from the 17...
- Q22. SRX Series device enrollment with Policy Enforcer fails To debug further, the user issues ...
- Q23. Your IPsec tunnel is configured with multiple security associations (SAs). Your SRX Series...
- Q24. Your IPsec VPN configuration uses two CoS forwarding classes to separate voice and data tr...
- Q25. Which two statements are true regarding NAT64? (Choose two.)...
- Q26. Exhibit (Exhibit) You configure Source NAT using a pool of addresses that are in the same ...
- Q27. In Juniper ATP Cloud, what are two different actions available in a threat prevention poli...
- Q28. You are not able to activate the SSH honeypot on the all-in-one Juniper ATP appliance. Wha...
- Q29. Exhibit (Exhibit) Referring to the exhibit, an internal host is sending traffic to an Inte...
- Q30. Refer to the Exhibit: (Exhibit) Which two statements about the configuration shown in the ...
- Q31. You want to deploy two vSRX instances in different public cloud providers to provide redun...
- Q32. Exhibit: (Exhibit) Referring to the exhibit, a default static route on SRX-1 sends all tra...
- Q33. Click the Exhibit button. (Exhibit) Which type of NAT is shown in the exhibit?...
- Q34. The monitor traffic interface command is being used to capture the packets destined to and...
- Q35. You are asked to detect domain generation algorithms Which two steps will accomplish this ...
- Q36. You are asked to share threat intelligence from your environment with third party tools so...
- Q37. Exhibit. (Exhibit) Referring to the exhibit, which two statements are true? (Choose two.)...
- Q38. You must setup a Ddos solution for your ISP. The solution must be agile and not block legi...
- Q39. You want to configure a threat prevention policy. Which three profiles are configurable in...
- Q40. Exhibit: (Exhibit) You have configured a CoS-based VPN that is not functioning correctly. ...
- Q41. You configure two Ethernet interfaces on your SRX Series device as Layer 2 interfaces and ...
- Q42. You want to use selective stateless packet-based forwarding based on the source address. I...
- Q43. You have designed the firewall filter shown in the exhibit to limit SSH control traffic to...
- Q44. Your customer needs embedded security in an EVPN-VXLAN solution. What are two benefits of ...
- Q45. Your organization has multiple Active Directory domain to control user access. You must en...
- Q46. Exhibit (Exhibit) Which two statements are correct about the output shown in the exhibit? ...
- Q47. Exhibit (Exhibit) Referring to the exhibit, which two statements are true about the CAK st...
- Q48. What is the advantage of using separate st0 logical units for each spoke connection?...
- Q49. You want to enable inter-tenant communicaon with tenant system. In this Scenario, which tw...
- Q50. Exhibit: (Exhibit) In which mode is the SRX Series device?...
- Q51. Exhibit: (Exhibit) Referring to the exhibit, which two statements are correct? (Choose two...
- Q52. Refer to the exhibit, (Exhibit) which two potential violations will generate alarm ? (Choo...
- Q53. You are configuring an interconnect logical system that is configured as a VPLS switch to ...
- Q54. You want to use a security profile to limit the system resources allocated to user logical...
- Q55. You issue the command shown in the exhibit. Which policy will be active for the identified...
- Q56. In an effort to reduce client-server latency transparent mode was enabled an SRX series de...
- Q57. What are two important function of the Juniper Networks ATP appliance solution? (Choose tw...
- Q58. You are asked to establish IBGP between two nodes, but the session is not established. To ...
- Q59. In a multinode HA environment, which service must be configured to synchronize between nod...
- Q60. Exhibit: (Exhibit) Referring to the exhibit, which two statements are correct?...
- Q61. Exhibit. (Exhibit) A hub member of an ADVPN is not functioning correctly. Referring the ex...
- Q62. Exhibit (Exhibit) Referring to the exhibit, which two statements are true? (Choose two.)...
- Q63. You have an initial setup of ADVPN with two spokes and a hub. A host at partner Spoke-1 is...
- Q64. You are asked to configure tenant systems. Which two statements are true in this scenario?...
- Q65. Exhibit (Exhibit) You areasked to establish an IBGP peering between the SRX Series device ...
- Q66. Exhibit: (Exhibit) You have deployed an SRX Series device as shown in the exhibit. The dev...
- Q67. Exhibit: (Exhibit) Referring to the exhibit, your company's infrastructure team implemente...
- Q68. Your company wants to use the Juniper Seclntel feeds to block access to known command and ...
- Q69. Exhibit: (Exhibit) Referring to the exhibit, which two statements are true? (Choose two.)...
- Q70. Exhibit (Exhibit) Which statement is true about the output shown in the exhibit?...
- Q71. You are asked to deploy Juniper atp appliance in your network. You must ensure that incide...
- Q72. You are deploying threat remediation to endpoints connected through third-party devices. I...
- Q73. You are connecting two remote sites to your corporate headquarters site.You must ensure th...
- Q74. Exhibit: (Exhibit) You are asked to ensure that Internet users can access the company's in...
- Q75. You need to set up source NAT so that external hosts can initiate connections to an intern...
- Q76. Exhibit (Exhibit) You have configured the SRX Series device to switch packets for multiple...


