Join the discussion
Question 1/215
Select the correct sequence for the information security risk assessment process in an ISMS.
To complete the sequence click on the blank section you want to complete so that it is highlighted in red, and then click on the applicable text from the options below. Alternatively, you may drag and drop the options to the appropriate blank
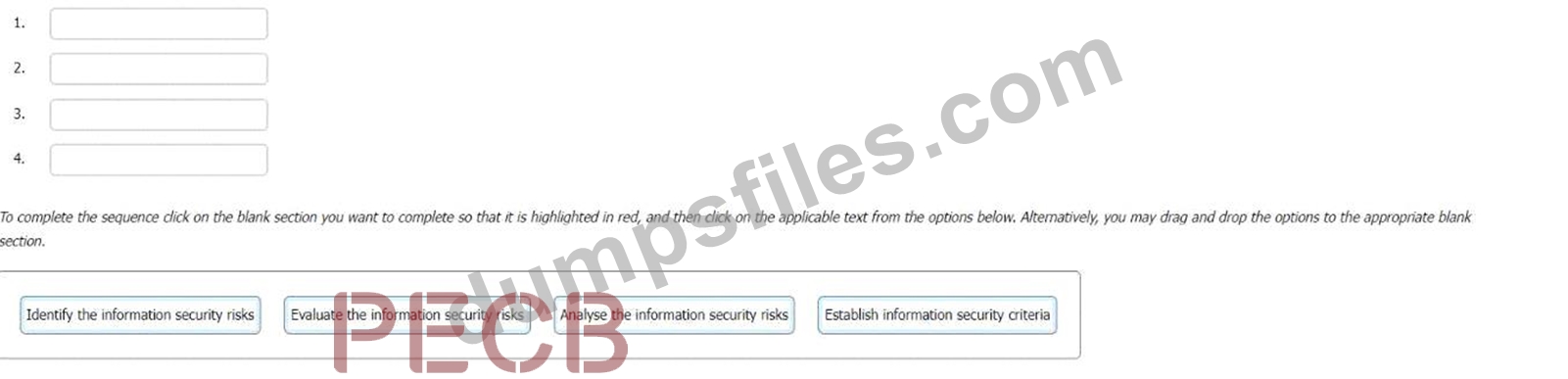
To complete the sequence click on the blank section you want to complete so that it is highlighted in red, and then click on the applicable text from the options below. Alternatively, you may drag and drop the options to the appropriate blank

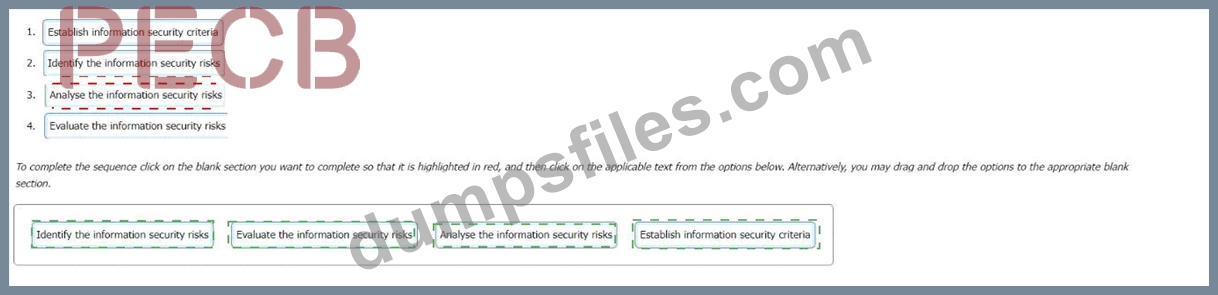
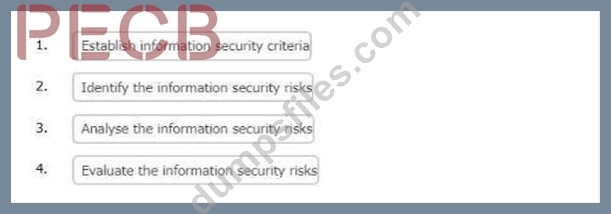
Correct Answer:
Explanation:
A group of black text Description automatically generated
According to ISO 27001:2022, the standard for information security management systems (ISMS), the correct sequence for the information security risk assessment process is as follows:
Establish information security criteria
Identify the information security risks
Analyse the information security risks
Evaluate the information security risks
The first step is to establish the information security criteria, which include the risk assessment methodology, the risk acceptance criteria, and the risk evaluation criteria. These criteria define how the organization will perform the risk assessment, what level of risk is acceptable, and how the risks will be compared and prioritized.
The second step is to identify the information security risks, which involve identifying the assets, threats, vulnerabilities, and existing controls that are relevant to the ISMS. The organization should also identify the potential consequences and likelihood of each risk scenario.
The third step is to analyse the information security risks, which involve estimating the level of risk for each risk scenario based on the criteria established in the first step. The organization should also consider the sources of uncertainty and the confidence level of the risk estimation.
The fourth step is to evaluate the information security risks, which involve comparing the estimated risk levels with the risk acceptance criteria and determining whether the risks are acceptable or need treatment. The organization should also prioritize the risks based on the risk evaluation criteria and the objectives of the ISMS.
References: ISO 27001:2022 Clause 6.1.2 Information security risk assessment, ISO 27001 Risk Assessment
& Risk Treatment: The Complete Guide - Advisera, ISO 27001 Risk Assessment: 7 Step Guide - IT Governance UK Blog
Add Comments
- Other Question (215q)
- Q1. Select the correct sequence for the information security risk assessment process in an ISM...
- Q2. You are an experienced ISMS audit team leader, assisting an auditor in training to write t...
- Q3. You are an ISMS audit team leader assigned by your certification body to carry out a follo...
- Q4. In the event of an Information security incident, system users' roles and responsibilities...
- Q5. You are an experienced ISMS audit team leader guiding an auditor in training. You decide t...
- Q6. Scenario 5: Data Grid Inc. is a well-known company that delivers security services across ...
- Q7. You are conducting an ISMS audit in the despatch department of an international logistics ...
- Q8. In the event of an Information security incident, system users' roles and responsibilities...
- Q9. You are an experienced ISMS audit team leader. During the conducting of a third-party surv...
- Q10. Auditors need to communicate effectively with auditees. Therefore, their personal behaviou...
- Q11. Select the words that best complete the sentence below to describe audit resources: (Exhib...
- Q12. Which two of the following phrases would apply to "act" in relation to the Plan-Do-Check-A...
- Q13. You are the audit team leader conducting a third-party audit of an online insurance compan...
- Q14. Which six of the following actions are the individual(s) managing the audit programme resp...
- Q15. Scenario 8: EsBank provides banking and financial solutions to the Estonian banking sector...
- Q16. You are performing an ISMS audit at a residential nursing home that provides healthcare se...
- Q17. Which of the following is a preventive security measure?...
- Q18. Which two of the following statements are true?...
- Q19. You are the lead auditor of the courier company SpeeDelivery. You have carried out a risk ...
- Q20. What is the security management term for establishing whether someone's identity is correc...
- Q21. You are carrying out your first third-party ISMS surveillance audit as an Audit Team Leade...
- Q22. The responsibilities of a------------ include facilitating audit activities, maintaining l...
- Q23. Select two options that describe an advantage of using a checklist....
- Q24. Scenario 7: Lawsy is a leading law firm with offices in New Jersey and New York City. It h...
- Q25. Availability means
- Q26. You are performing an ISMS audit at a nursing home where residents always wear an electron...
- Q27. Which two activities align with the "Check'' stage of the Plan-Do-Check-Act cycle when app...
- Q28. You are performing an ISMS audit at a residential nursing home (ABC) that provides healthc...
- Q29. During a follow-up audit, you notice that a nonconformity identified for completion before...
- Q30. Scenario 6: Sinvestment is an insurance company that offers home, commercial, and life ins...
- Q31. Which four of the following statements about audit reports are true?...
- Q32. Which one of the following options best describes the purpose of a Stage 2 audit?...
- Q33. You are performing an ISMS audit at a European-based residential nursing home called ABC t...
- Q34. CEO sends a mail giving his views on the status of the company and the company's future st...
- Q35. You are a certification body auditor, conducting a surveillance audit to ISO/IEC 27001:202...
- Q36. Scenario 8: EsBank provides banking and financial solutions to the Estonian banking sector...
- Q37. What is social engineering?
- Q38. Which is not a requirement of HR prior to hiring?...
- Q39. (Exhibit)
- Q40. After a fire has occurred, what repressive measure can be taken?...
- Q41. Scenario 6: Sinvestment is an insurance company that offers home, commercial, and life ins...
- Q42. Select the correct sequence for the information security risk assessment process in an ISM...
- Q43. You are conducting an ISMS audit. The next step in your audit plan is to verify that the o...
- Q44. Your organisation is currently seeking ISO/IEC27001:2022 certification. You have just qual...
- Q45. We can leave laptops during weekdays or weekends in locked bins....
- Q46. Select the words that best complete the sentence: To complete the sentence with the best w...
- Q47. How does the use of new technologies such as big data impact auditing?...
- Q48. Why do we need to test a disaster recovery plan regularly, and keep it up to date?...
- Q49. You are an experienced ISMS audit team leader. An auditor in training has approached you t...
- Q50. You work in the office of a large company. You receive a call from a person claiming to be...
- Q51. In the context of a management system audit, please identify the sequence of a typical pro...
- Q52. Select the words that best complete the sentence: To complete the sentence with the word(s...
- Q53. A hacker gains access to a web server and reads the credit card numbers stored on that ser...
- Q54. You are the lead auditor of the courier company SpeeDelivery. You have carried out a risk ...
- Q55. You are performing an ISO 27001 ISMS surveillance audit at a residential nursing home, ABC...
- Q56. What is the goal of classification of information?...
- Q57. You are an ISMS audit team leader tasked with conducting a follow-up audit at a client's d...
- Q58. You ask the IT Manager why the organisation still uses the mobile app while personal data ...
- Q59. In regard to generating an audit finding, select the words that best complete the followin...
- Q60. Changes to the information processing facilities shall be done in controlled manner....
- Q61. Which two options are benefits of third-party accredited certification of information secu...
- Q62. You are an ISMS audit team leader preparing to chair a closing meeting following a third-p...
- Q63. You are an experienced ISMS audit team leader, talking to an Auditor in training who has b...
- Q64. Which two of the following statements are true?...
- Q65. Which threat could occur if no physical measures are taken?...
- Q66. Which option below is NOT a role of the audit team leader?...
- Q67. Phishing is what type of Information Security Incident?...
- Q68. What is the worst possible action that an employee may receive for sharing his or her pass...
- Q69. Implement plan on a test basis - this comes under which section of PDCA...
- Q70. You are an experienced ISMS audit team leader. During the conducting of a third-party surv...
- Q71. You are an experienced ISMS audit team leader guiding an auditor in training. You are test...
- Q72. As the ISMS audit team leader, you are conducting a second-party audit of an international...
- Q73. An organisation is looking for management system initial certification. Please identify th...
- Q74. What is the standard definition of ISMS?
- Q75. You are an ISMS audit team leader tasked with conducting a follow-up audit at a client's d...
- Q76. You are performing an ISMS audit at a residential nursing home called ABC that provides he...
- Q77. Which of the following statements are correct for Clean Desk Policy?...
- Q78. You are the audit team leader conducting a third-party audit of an online insurance compan...
- Q79. In acceptable use of Information Assets, which is the best practice?...
- Q80. You have just completed a scheduled information security audit of your organisation when t...
- Q81. Cabling Security is associated with Power, telecommunication and network cabling carrying ...
- Q82. All are prohibited in acceptable use of information assets, except:...
- Q83. In the context of a management system audit, please identify the sequence of a typical pro...
- Q84. During a third-party certification audit, you are presented with a list of issues by an au...
- Q85. You are an experienced ISMS audit team leader guiding an auditor in training. You decide t...
- Q86. A key audit process is the way auditors gather information and determine the findings' cha...
- Q87. Availability means
- Q88. Which of the following is a preventive security measure?...
- Q89. You are conducting an ISMS audit in the despatch department of an international logistics ...
- Q90. Select the words that best complete the sentence: To complete the sentence with the word(s...
- Q91. You receive the following mail from the IT support team: Dear User,Starting next week, we ...
- Q92. After a fire has occurred, what repressive measure can be taken?...
- Q93. All are prohibited in acceptable use of information assets, except:...
- Q94. You receive the following mail from the IT support team: Dear User,Starting next week, we ...
- Q95. Who is responsible for Initial asset allocation to the user/custodian of the assets?...
- Q96. You are an experienced audit team leader guiding an auditor in training. Your team is curr...
- Q97. You are the person responsible for managing the audit programme and deciding the size and ...
- Q98. Scenario 9: UpNet, a networking company, has been certified against ISO/IEC 27001. It prov...
- Q99. You are an experienced ISMS audit team leader who is currently conducting a third party in...
- Q100. You are conducting an ISMS audit. The next step in your audit plan is to verify that the o...
- Q101. Which one of the following options best describes the main purpose of a Stage 1 third-part...
- Q102. You are conducting an ISMS audit in the despatch department of an international logistics ...
- Q103. You are an experienced ISMS audit team leader guiding an auditor in training. Your team ha...
- Q104. An employee caught with offense of abusing the internet, such as P2P file sharing or video...
- Q105. You are an audit team leader conducting a third-party surveillance audit of a telecom serv...
- Q106. Which of the following is not a type of Information Security attack?...
- Q107. CMM stands for?
- Q108. You are an audit team leader who has just completed a third-party audit of a mobile teleco...
- Q109. The computer room is protected by a pass reader. Only the System Management department has...
- Q110. Often, people do not pick up their prints from a shared printer. How can this affect the c...
- Q111. Information Security is a matter of building and maintaining ________ ....
- Q112. An employee caught temporarily storing an MP3 file in his workstation will not receive an ...
- Q113. Which is not a requirement of HR prior to hiring?...
- Q114. Which of the following is an information security management system standard published by ...
- Q115. What is a reason for the classification of information?...
- Q116. A couple of years ago you started your company which has now grown from 1 to 20 employees....
- Q117. Which three of the following work documents are not required for audit planning by an audi...
- Q118. Who are allowed to access highly confidential files?...
- Q119. You are performing an ISMS audit at a residential nursing home railed ABC that provides he...
- Q120. What is the difference between a restricted and confidential document?...
- Q121. There is a network printer in the hallway of the company where you work. Many employees do...
- Q122. You are carrying out your first third-party ISMS surveillance audit as an Audit Team Leade...
- Q123. The following are definitions of Information, except:...
- Q124. Who is responsible for Initial asset allocation to the user/custodian of the assets?...
- Q125. You are an experienced ISMS audit team leader. You are providing an introduction to ISO/IE...
- Q126. You have a hard copy of a customer design document that you want to dispose off. What woul...
- Q127. After analyzing the audit conclusions, Company X decided to accept the risk related to one...
- Q128. There is a scheduled fire drill in your facility. What should you do?...
- Q129. In what part of the process to grant access to a system does the user present a token?...
- Q130. You are carrying out your first third-party ISMS surveillance audit as an audit team leade...
- Q131. What is a reason for the classification of information?...
- Q132. Select the words that best complete the sentence below to describe a third-party audit pla...
- Q133. The following are the guidelines to protect your password, except:...
- Q134. You are the audit team leader conducting a third-party audit of an online insurance compan...
- Q135. A fire breaks out in a branch office of a health insurance company. The personnel are tran...
- Q136. Scenario 8: EsBank provides banking and financial solutions to the Estonian banking sector...
- Q137. You are an experienced ISMS audit team leader who is currently conducting a third party in...
- Q138. Select a word from the following options that best completes the sentence: To complete the...
- Q139. The audit team leader prepares the audit plan for an initial certification stage 2 audit t...
- Q140. You are an experienced ISMS internal auditor. You have just completed a scheduled informat...
- Q141. You are performing an ISMS audit at a residential nursing home called ABC that provides he...
- Q142. You are conducting an ISMS audit in the despatch department of an international logistics ...
- Q143. You are conducting a third-party surveillance audit when another member of the audit team ...
- Q144. Below is Purpose of "Integrity", which is one of the Basic Components of Information Secur...
- Q145. You are performing an ISMS audit at a residential nursing home that provides healthcare se...
- Q146. During a third-party certification audit, you are presented with a list of issues by an au...
- Q147. You are an ISMS audit team leader tasked with conducting a follow-up audit at a client's d...
- Q148. A planning process that introduced the concept of planning as a cycle that forms the basis...
- Q149. What is the worst possible action that an employee may receive for sharing his or her pass...
- Q150. You are performing an ISMS audit at a residential nursing home that provides healthcare se...
- Q151. We can leave laptops during weekdays or weekends in locked bins....
- Q152. In the event of an Information security incident, system users' roles and responsibilities...
- Q153. The data center at which you work is currently seeking ISO/IEC27001:2022 certification. In...
- Q154. The data center at which you work is currently seeking ISO/IEC27001:2022 certification. In...
- Q155. Cabling Security is associated with Power, telecommunication and network cabling carrying ...
- Q156. What is the security management term for establishing whether someone's identity is correc...
- Q157. An employee caught with offense of abusing the internet, such as P2P file sharing or video...
- Q158. Select the words that best complete the sentence: To complete the sentence with the best w...
- Q159. You work in the office of a large company. You receive a call from a person claiming to be...
- Q160. During a Stage 1 audit opening meeting, the Management System Representative (MSR) asks to...
- Q161. Which two activities align with the "Check'' stage of the Plan-Do-Check-Act cycle when app...
- Q162. You are an experienced ISMS audit team leader, assisting an auditor in training to write t...
- Q163. All are prohibited in acceptable use of information assets, except:...
- Q164. Based on the identified nonconformities. Company A established action plans that included ...
- Q165. Auditor competence is a combination of knowledge and skills. Which two of the following ac...
- Q166. A well-executed risk analysis provides a great deal of useful information. A risk analysis...
- Q167. You receive an E-mail from some unknown person claiming to be representative of your bank ...
- Q168. A key audit process is the way auditors gather information and determine the findings' cha...
- Q169. Which six of the following actions are the individual(s) managing the audit programme resp...
- Q170. (Exhibit)
- Q171. The following are definitions of Information, except:...
- Q172. Please match the roles to the following descriptions: (Exhibit) To complete the table clic...
- Q173. As the ISMS audit team leader, you are conducting a second-party audit of an international...
- Q174. You are performing an ISMS initial certification audit at a residential nursing home that ...
- Q175. You receive an E-mail from some unknown person claiming to be representative of your bank ...
- Q176. Select the words that best complete the sentence to describe an audit finding. (Exhibit)...
- Q177. You are an experienced audit team leader guiding an auditor in training. Your team is curr...
- Q178. Which two of the following actions are the individual(s) managing the audit programme resp...
- Q179. You are performing an ISMS audit at a European-based residential nursing home called ABC t...
- Q180. You are an experienced ISMS audit team leader providing guidance to an ISMS auditor in tra...
- Q181. Select the words that best complete the sentence to describe an audit finding. (Exhibit)...
- Q182. You are performing an ISMS initial certification audit at a residential nursing home that ...
- Q183. You are an experienced ISMS audit team leader providing instruction to an auditor in train...
- Q184. What type of compliancy standard, regulation or legislation provides a code of practice fo...
- Q185. Select the words that best complete the sentence: To complete the sentence with the word(s...
- Q186. CMM stands for?
- Q187. You are an ISMS auditor conducting a third-party surveillance audit of a telecom's provide...
- Q188. You are an experienced ISMS audit team leader providing instruction to an auditor in train...
- Q189. Which two of the following options do not participate in a first-party audit?...
- Q190. Which of the following is a possible event that can have a disruptive effect on the reliab...
- Q191. Which three of the following phrases are objectives' in relation to an audit?...
- Q192. Which two of the following phrases would apply to "act" in relation to the Plan-Do-Check-A...
- Q193. Which two of the following phrases would apply to "plan" in relation to the Plan-Do-Check-...
- Q194. Select a word from the following options that best completes the sentence: To complete the...
- Q195. What type of system ensures a coherent Information Security organisation?...
- Q196. Scenario 6: Sinvestment is an insurance company that offers home, commercial, and life ins...
- Q197. You are an experienced ISMS audit team leader, talking to an Auditor in training who has b...
- Q198. An administration office is going to determine the dangers to which it is exposed. What do...
- Q199. You are preparing the audit findings. Select two options that are correct....
- Q200. In the context of a third-party certification audit, confidentiality is an issue in an aud...
- Q201. You are performing an ISMS initial certification audit at a residential nursing home that ...
- Q202. You are an ISMS auditor conducting a third-party surveillance audit of a telecom's provide...
- Q203. Which two of the following phrases would apply to "plan" in relation to the Plan-Do-Check-...
- Q204. You are performing an ISMS initial certification audit at a residential nursing home that ...
- Q205. You received an email requiring you to send information such as name, email, and password ...
- Q206. You have just completed a scheduled information security audit of your organisation when t...
- Q207. You are conducting an ISMS audit in the despatch department of an international logistics ...
- Q208. You are an experienced ISMS audit team leader. An auditor in training has approached you t...
- Q209. You have a hard copy of a customer design document that you want to dispose off. What woul...
- Q210. Which measure is a preventive measure?
- Q211. Which of the following is not a type of Information Security attack?...
- Q212. What is a reason for the classification of information?...
- Q213. You are an experienced ISMS audit team leader providing instruction to an auditor in train...
- Q214. During a third-party certification audit, you are presented with a list of issues by an au...
- Q215. __________ is a software used or created by hackers to disrupt computer operation, gather ...

[×]
Download PDF File
Enter your email address to download PECB.ISO-IEC-27001-Lead-Auditor.v2025-01-11.q215.pdf

