Join the discussion
Question 1/108
Given the following RQL:
event from cloud.audit_logs where operation IN ('CreateCryptoKey', 'DestroyCryptoKeyVersion',
'v1.compute.disks.createSnapshot')
Which audit event snippet is identified?
A)
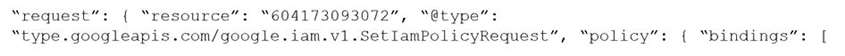
B)

C)
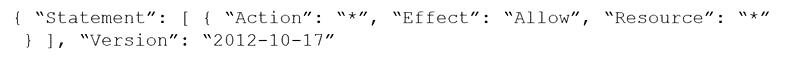
D)

event from cloud.audit_logs where operation IN ('CreateCryptoKey', 'DestroyCryptoKeyVersion',
'v1.compute.disks.createSnapshot')
Which audit event snippet is identified?
A)
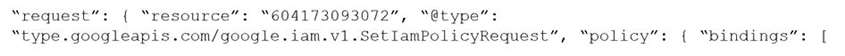
B)

C)
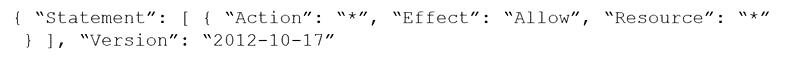
D)

Correct Answer: D
Add Comments
- Other Question (108q)
- Q1. Given the following RQL: event from cloud.audit_logs where operation IN ('CreateCryptoKey'...
- Q2. You are an existing customer of Prisma Cloud Enterprise. You want to onboard a public clou...
- Q3. Which Defender type performs registry scanning?...
- Q4. Match the correct scanning mode for each given operation. (Select your answer from the pul...
- Q5. Which file extension type is supported for Malware scanning in Prisma Cloud Data Security ...
- Q6. Given the following RQL: (Exhibit) Which audit event snippet is identified by the RQL? A) ...
- Q7. An administrator has access to a Prisma Cloud Enterprise What are the steps to deploy a si...
- Q8. The development team wants to fail CI jobs where a specific CVE is contained within the im...
- Q9. Which of the following are correct statements regarding the use of access keys? (Choose tw...
- Q10. Which data security default policy is able to scan for vulnerabilities?...
- Q11. An administrator needs to write a script that automatically deactivates access keys that h...
- Q12. Which two services require external notifications to be enabled for policy violations in t...
- Q13. Order the steps involved in onboarding an AWS Account for use with Data Security feature. ...
- Q14. One of the resources on the network has triggered an alert for a Default Config policy. Gi...
- Q15. Which authentication mechanism is supported by Prisma Cloud?...
- Q16. During an initial deployment of Prisma Cloud Compute, the customer sees vulnerabilities in...
- Q17. The development team wants to fail CI jobs where a specific CVE is contained within the im...
- Q18. A customer has configured the JIT, and the user created by the process is trying to log in...
- Q19. An S3 bucket within AWS has generated an alert by violating the Prisma Cloud Default polic...
- Q20. Which two IDE plugins are supported by Prisma Cloud as part of its DevOps Security? (Choos...
- Q21. What are two ways to scan container images in Jenkins pipelines? (Choose two )...
- Q22. A security team notices a number of anomalies under Monitor > Events. The incident resp...
- Q23. The security auditors need to ensure that given compliance checks are being run on the hos...
- Q24. Which two statements apply to the Defender type Container Defender - Linux?...
- Q25. An administrator sees that a runtime audit has been generated for a host. The audit messag...
- Q26. The development team wants to fail CI jobs where a specific CVE is contained within the im...
- Q27. Which two variables must be modified to achieve automatic remediation for identity and acc...
- Q28. A customer has a development environment with 50 connected Defenders A maintenance window ...
- Q29. Which of the below actions would indicate - "The timestamp on the compliance dashboard?...
- Q30. A customer wants to scan a serverless function as part of a build process. Which twistcli ...
- Q31. Which statement accurately characterizes SSO Integration on Prisma Cloud?...
- Q32. Which intensity setting for anomaly alerts is used for the measurement of 100 events over ...
- Q33. A customer wants to monitor the company's AWS accounts via Prisma Cloud, but only needs th...
- Q34. Review this admission control policy: match[{"msg": msg}] { input.request.operation == "CR...
- Q35. An administrator sees that a runtime audit has been generated for a host. The audit messag...
- Q36. A DevOps lead reviewed some system logs and notices some odd behavior that could be a data...
- Q37. Match the correct scanning mode for each given operation. (Select your answer from the pul...
- Q38. A Prisma Cloud administrator is tasked with pulling a report via API. The Prisma Cloud ten...
- Q39. The security team wants to protect a web application container from an SQLi attack? Which ...
- Q40. The exclamation mark on the resource explorer page would represent?...
- Q41. The attempted bytes count displays?
- Q42. You are tasked with configuring a Prisma Cloud build policy for Terraform. What type of qu...
- Q43. Which step is included when configuring Kubernetes to use Prisma Cloud Compute as an admis...
- Q44. What is the order of steps in a Jenkins pipeline scan? (Drag the steps into the correct or...
- Q45. A security team notices a number of anomalies under Monitor > Events The incident respo...
- Q46. An administrator wants to enforce a rate limit for users not being able to post five (5) ....
- Q47. An administrator wants to install the Defenders to a Kubernetes cluster. This cluster is r...
- Q48. The Compute Console has recently been upgraded, and the administrator plans to delay upgra...
- Q49. Which statement is true regarding CloudFormation templates?...
- Q50. Which options show the steps are required to upgrade Console when using projects?...
- Q51. An administrator wants to retrieve the compliance policies for images scanned in a continu...
- Q52. How are the following categorized? * Backdoor account access * Hijacked processes * Latera...
- Q53. Which order of steps map a policy to a custom compliance standard? (Drag the steps into th...
- Q54. Which three fields are mandatory when authenticating the Prisma Cloud plugin in the Intell...
- Q55. The security team wants to enable the "block" option under compliance checks on the host. ...
- Q56. Which two integrations enable ingesting host findings to generate alerts? (Choose two.)...
- Q57. You wish to create a custom policy with build and run subtypes. Match the query types for ...
- Q58. Which three types of runtime rules can be created? (Choose three.)...
- Q59. Given an existing ECS Cluster, which option shows the steps required to install the Consol...
- Q60. The Unusual protocol activity (Internal) network anomaly is generating too many alerts. An...
- Q61. A customer has Defenders connected to Prisma Cloud Enterprise The Defenders are deployed a...
- Q62. Match the service on the right that evaluates each exposure type on the left. (Select your...
- Q63. A customer is interested in PCI requirements and needs to ensure that no privilege contain...
- Q64. Which type of query is used for scanning Infrastructure as Code (laC) templates?...
- Q65. You are an existing customer of Prisma Cloud Enterprise. You want to onboard a public clou...
- Q66. Given this information: The Console is located at https://prisma-console.mydomain.local Th...
- Q67. A customer finds that an open alert from the previous day has been resolved. No auto-remed...
- Q68. An administrator has deployed Console into a Kubernetes cluster running in AWS. The admini...
- Q69. Where can Defender debug logs be viewed? (Choose two.)...
- Q70. Put the steps involved to configure and scan using the IntelliJ plugin in the correct orde...
- Q71. Which order of steps map a policy to a custom compliance standard? (Drag the steps into th...
- Q72. A customer wants to scan a serverless function as part of a build process. Which twistcli ...
- Q73. An administrator needs to write a script that automatically deactivates access keys that h...
- Q74. Which order of steps map a policy to a custom compliance standard? (Drag the steps into th...
- Q75. What are two key requirements for integrating Okta with Prisma Cloud when multiple Amazon ...
- Q76. Order the steps involved in onboarding an AWS Account for use with Data Security feature. ...
- Q77. The compliance team needs to associate Prisma Cloud policies with compliance frameworks. W...
- Q78. Which two bot types are part of Web Application and API Security (WAAS) bot protection? (C...
- Q79. Order the steps involved in onboarding an AWS Account for use with Data Security feature. ...
- Q80. Which two attributes of policies can be fetched using API? (Choose two.)...
- Q81. The administrator wants to review the Console audit logs from within the Console. Which pa...
- Q82. Which statement is true about obtaining Console images for Prisma Cloud Compute Edition?...
- Q83. Which role must be assigned to DevOps users who need access to deploy Container and Host D...
- Q84. Given a default deployment of Console, a customer needs to identify the alerted compliance...
- Q85. An administrator has deployed Console into a Kubernetes cluster running in AWS. The admini...
- Q86. A customer wants to turn on Auto Remediation. Which policy type has the built-in CLI comma...
- Q87. A customer has a requirement to scan serverless functions for vulnerabilities. Which three...
- Q88. How are the following categorized? Backdoor account access Hijacked processes Lateral move...
- Q89. A customer has a requirement to terminate any Container from image topSecret:latest when a...
- Q90. A manager informs the SOC that one or more RDS instances have been compromised and the SOC...
- Q91. A customer finds that an open alert from the previous day has been resolved. No auto-remed...
- Q92. The security team wants to target a CNAF policy for specific running Containers. How shoul...
- Q93. Which step is included when configuring Kubernetes to use Prisma Cloud Compute as an admis...
- Q94. What is the order of steps in a Jenkins pipeline scan? (Drag the steps into the correct or...
- Q95. Web-Application and API Security (WAAS) provides protection for which two protocols? (Choo...
- Q96. Which categories does the Adoption Advisor use to measure adoption progress for Cloud Secu...
- Q97. Which method should be used to authenticate to Prisma Cloud Enterprise programmatically?...
- Q98. Which two options may be used to upgrade the Defenders with a Console v20.04 and Kubernete...
- Q99. An administrator has a requirement to ingest all Console and Defender logs to Splunk. Whic...
- Q100. A customer wants to be notified about port scanning network activities in their environmen...
- Q101. An organization wants to be notified immediately to any "High Severity" alerts for the acc...
- Q102. In WAAS Access control file upload controls, which three file types are supported out of t...
- Q103. The development team wants to fail CI jobs where a specific CVE is contained within the im...
- Q104. Per security requirements, an administrator needs to provide a list of people who are rece...
- Q105. A DevOps lead reviewed some system logs and notices some odd behavior that could be a data...
- Q106. Which two filters are available in the SecOps dashboard? (Choose two.)...
- Q107. The Prisma Cloud administrator has configured a new policy. Which steps should be used to ...
- Q108. Which statement is true about obtaining Console images for Prisma Cloud Compute Edition?...

[×]
Download PDF File
Enter your email address to download PaloAltoNetworks.PCCSE.v2024-02-21.q108.pdf

