Join the discussion
Question 1/231
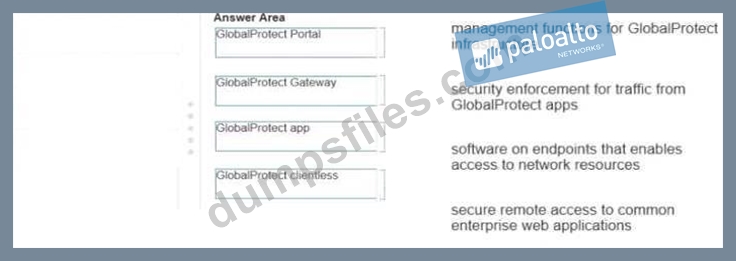
Drag and Drop Question
Match each GlobalProtect component to the purpose of that component.

Match each GlobalProtect component to the purpose of that component.

Correct Answer:
Add Comments
- Other Question (231q)
- Q1. Drag and Drop Question Match each GlobalProtect component to the purpose of that component...
- Q2. Refer to the exhibit. (Exhibit) An administrator is using DNAT to map two servers to a sin...
- Q3. An administrator is using Panorama to manage me and suspects an IKE Crypto mismatch betwee...
- Q4. A network-security engineer attempted to configure a bootstrap package on Microsoft Azure,...
- Q5. Using multiple templates in a stack to manage many firewalls provides which two advantages...
- Q6. Which steps should an engineer take to forward system logs to email?...
- Q7. The same route appears in the routing table three times using three different protocols Wh...
- Q8. Which three firewall states are valid? (Choose three.)...
- Q9. What is the URL for the full list of applications recognized by Palo Alto Networks?...
- Q10. When setting up a security profile which three items can you use? (Choose three )...
- Q11. An administrator wants to upgrade an NGFW from PAN-OS® 9.0 to PAN-OS® 10.0. The firewall i...
- Q12. Which feature prevents the submission of corporate login information into website forms?...
- Q13. An administrator is using Panorama and multiple Palo Alto Networks NGFWs. After upgrading ...
- Q14. Which three authentication factors does PAN-OS® software support for MFA (Choose three.)...
- Q15. SAML SLO is supported for which two firewall features? (Choose two.)...
- Q16. An administrator wants multiple web servers in the DMZ to receive connections initiated fr...
- Q17. If malware is detected on the internet perimeter, what other places in the network might b...
- Q18. A firewall administrator has completed most of the steps required to provision a standalon...
- Q19. An administrator needs to determine why users on the trust zone cannot reach certain websi...
- Q20. A customer is replacing their legacy remote access VPN solution The current solution is in...
- Q21. An administrator wants multiple web servers in the DMZ to receive connections initiated fr...
- Q22. An administrator needs to upgrade an NGFW to the most current version of PAN-OS® software....
- Q23. Select all the platform components that Wildfire automatically updates after finding malic...
- Q24. To more easily reuse templates and template slacks , you can create term plate variables i...
- Q25. An administrator cannot see any Traffic logs from the Palo Alto Networks NGFW in Panorama ...
- Q26. What are three valid actions in a File Blocking Profile? (Choose three)...
- Q27. Refer to exhibit. (Exhibit) An organization has Palo Alto Networks NGFWs that send logs to...
- Q28. An administrator deploys PA-500 NGFWs as an active/passive high availability pair. The dev...
- Q29. An engineer has been tasked with reviewing traffic logs to find applications the firewall ...
- Q30. Below are the steps in the workflow for creating a Best Practice Assessment in a firewall ...
- Q31. As a best practice, which URL category should you target first for SSL decryption*?...
- Q32. SAML SLO is supported for which two firewall features? (Choose two.)...
- Q33. A network security administrator has an environment with multiple forms of authentication....
- Q34. Which three options are supported in HA Lite? (Choose three.)...
- Q35. Which processing order will be enabled when a Panorama administrator selects the setting "...
- Q36. An engineer wants to implement the Palo Alto Networks firewall in VWire mode on the intern...
- Q37. An engineer is bootstrapping a VM-Series Firewall Other than the 'config folder, which thr...
- Q38. A customer wants to combine multiple Ethernet interfaces into a single virtual interface u...
- Q39. Refer to the exhibit. (Exhibit) Which certificates can be used as a Forwarded Trust certif...
- Q40. Which option would an administrator choose to define the certificate and protocol that Pan...
- Q41. A firewall administrator is troubleshooting problems with traffic passing through the Palo...
- Q42. Which two mechanisms help prevent a spilt brain scenario an Active/Passive High Availabili...
- Q43. An administrator plans to deploy 15 firewalls to act as GlobalProtect gateways around the ...
- Q44. Which CLI command is used to simulate traffic going through the firewall and determine whi...
- Q45. Which CLI command displays the current management plane memory utilization?...
- Q46. After configuring HA in Active/Passive mode on a pair of firewalls the administrator gets ...
- Q47. An engineer has been asked to limit which routes are shared by running two different areas...
- Q48. Which Security policy rule will allow an admin to block facebook chat but allow Facebook i...
- Q49. Which Panorama administrator types require the configuration of at least one access domain...
- Q50. Which CLI command enables an administrator to view details about the firewall including up...
- Q51. An administrator plans to deploy 15 firewalls to act as GlobalProtect gateways around the ...
- Q52. How would an administrator monitor/capture traffic on the management interface of the Palo...
- Q53. An organization is interested in migrating from their existing web proxy architecture to t...
- Q54. A firewall is configured with SSL Forward Proxy decryption and has the following four ente...
- Q55. An administrator receives the following error message: "IKE phase-2 negotiation failed whe...
- Q56. Which User-ID method maps IP addresses to usernames for users connecting through a web pro...
- Q57. A standalone firewall with local objects and policies needs to be migrated into Panorama. ...
- Q58. An administrator needs to upgrade an NGFW to the most current version of PAN-OS® software....
- Q59. True or False: DSRI degrades the performance of a firewall?...
- Q60. Match each type of DoS attack to an example of that type of attack (Exhibit)...
- Q61. The certificate information displayed in the following image is for which type of certific...
- Q62. What type of address object would be useful for internal devices where the addressing stru...
- Q63. Please match the terms to their corresponding definitions. (Exhibit)...
- Q64. How can a candidate or running configuration be copied to a host external from Panorama?...
- Q65. An administrator has created an SSL Decryption policy rule that decrypts SSL sessions on a...
- Q66. (Exhibit) What will be the source address in the ICMP packet?...
- Q67. A variable name must start with which symbol?
- Q68. Match each GlobalProtect component to the purpose of that component (Exhibit)...
- Q69. Which two benefits come from assigning a Decryption Profile to a Decryption policy rule wi...
- Q70. What are the major families of file types now supported by Wildfire in PAN-OS 7.0?...
- Q71. An administrator has 750 firewalls The administrator's central-management Panorama instanc...
- Q72. When configuring the firewall for packet capture, what are the valid stage types?...
- Q73. Exhibit: (Exhibit) What will be the egress interface if the traffic's ingress interface is...
- Q74. An administrator is using Panorama and multiple Palo Alto Networks NGFWs. After upgrading ...
- Q75. A security engineer needs to mitigate packet floods that occur on a set of servers behind ...
- Q76. An engineer needs to collect User-ID mappings from the company's existing proxies. What tw...
- Q77. An administrator is attempting to create policies tor deployment of a device group and tem...
- Q78. An administrator wants multiple web servers in the DMZ to receive connections initiated fr...
- Q79. Which URL Filtering Security Profile action logs the URL Filtering category to the URL Fil...
- Q80. (Exhibit) View the screenshots. A QoS profile and policy rules are configured as shown. Ba...
- Q81. Which two statements correctly describe Session 380280? (Choose two.) (Exhibit)...
- Q82. Refer to the exhibit. (Exhibit) Which will be the egress interface if the traffic's ingres...
- Q83. Which operation will impact the performance of the management plane?...
- Q84. A network administrator troubleshoots a VPN issue and suspects an IKE Crypto mismatch betw...
- Q85. Which three items are important considerations during SD-WAN configuration planning? (Choo...
- Q86. Refer to the diagram. (Exhibit) An administrator needs to create an address object that wi...
- Q87. An administrator is using Panorama and multiple Palo Alto Networks NGFWs. After upgrading ...
- Q88. A company is upgrading its existing Palo Alto Networks firewall from version 7.0.1 to 7.0....
- Q89. Refer to the exhibit. (Exhibit) An administrator cannot see any of the Traffic logs from t...
- Q90. Where is information about packet buffer protection logged?...
- Q91. A company has a policy that denies all applications it classifies as bad and permits only ...
- Q92. Click the Exhibit button below, (Exhibit) A firewall has three PBF rules and a default rou...
- Q93. What is the best description of the HA4 Keep-Alive Threshold (ms)?...
- Q94. An administrator wants to enable zone protection Before doing so, what must the administra...
- Q95. Given the following snippet of a WildFire submission log. did the end-user get access to t...
- Q96. An administrator using an enterprise PKI needs to establish a unique chain of trust to ens...
- Q97. Which two actions would be part of an automatic solution that would block sites with untru...
- Q98. Review the screenshot of the Certificates page. (Exhibit) An administrator tor a small LLC...
- Q99. An administrator has been asked to configure active/active HA for a pair of Palo Alto Netw...
- Q100. Based on the image, what caused the commit warning? (Exhibit)...
- Q101. With the default TCP and UDP settings on the firewall, what will be the identified applica...
- Q102. To more easily reuse templates and template stacks, you can create template variables in p...
- Q103. Which Panorama feature allows for logs generated by Panorama to be forwarded to an externa...
- Q104. Which two settings can be configured only locally on the firewall and not pushed from a Pa...
- Q105. Wildfire may be used for identifying which of the following types of traffic?...
- Q106. Refer to the exhibit. (Exhibit) Which certificates can be used as a Forwarded Trust certif...
- Q107. An administrator is building Security rules within a device group to block traffic to and ...
- Q108. Which two options are required on an M-100 appliance to configure it as a Log Collector? (...
- Q109. Which event will happen if an administrator uses an Application Override Policy?...
- Q110. An administrator has configured the Palo Alto Networks NGFW's management interface to conn...
- Q111. What are two characteristic types that can be defined for a variable? (Choose two )...
- Q112. When using the predefined default profile, the policy will inspect for viruses on the deco...
- Q113. Which three authentication factors does PAN-OS software support for MFA (Choose three.)...
- Q114. Which two subscriptions are available when configuring panorama to push dynamic updates to...
- Q115. Refer to the exhibit. (Exhibit) An administrator cannot see any of the Traffic logs from t...
- Q116. Refer to the exhibit. (Exhibit) A web server in the DMZ is being mapped to a public addres...
- Q117. When configuring a GlobalProtect Portal, what is the purpose of specifying an Authenticati...
- Q118. If the firewall has the link monitoring configuration, what will cause a failover? (Exhibi...
- Q119. Place the steps in the WildFire process workflow in their correct order. (Exhibit)...
- Q120. During SSL decryption which three factors affect resource consumption1? (Choose three )...
- Q121. When you configure an active/active high availability pair which two links can you use? (C...
- Q122. In a virtual router, which object contains all potential routes?...
- Q123. A network security engineer wants to prevent resource-consumption issues on the firewall. ...
- Q124. When backing up and saving configuration files, what is achieved using only the firewall a...
- Q125. Refer to the exhibit. (Exhibit) Which certificate can be used as the Forward Trust certifi...
- Q126. The certificate information displayed in the following image is for which type of certific...
- Q127. An administrator has created an SSL Decryption policy rule that decrypts SSL sessions on a...
- Q128. Which User-ID mapping method should be used in a high-security environment where all IP ad...
- Q129. A network security engineer is asked to provide a report on bandwidth usage. Which tab in ...
- Q130. Refer to the exhibit. (Exhibit) A web server in the DMZ is being mapped to a public addres...
- Q131. When using the predefined default profile, the policy will inspect for viruses on the deco...
- Q132. Which DoS protection mechanism detects and prevents session exhaustion attacks?...
- Q133. What happens when an A P firewall cluster synchronies IPsec tunnel security associations (...
- Q134. Which two settings can be configured only locally on the firewall and not pushed from a Pa...
- Q135. SAML SLO is supported for which two firewall features? (Choose two.)...
- Q136. Which three authentication factors does PAN-OS software support for MFA? (Choose three.)...
- Q137. If an administrator wants to decrypt SMTP traffic and possesses the server's certificate, ...
- Q138. An enterprise has a large Palo Alto Networks footprint that includes onsite firewalls and ...
- Q139. Which administrative authentication method supports authorization by an external service?...
- Q140. A prospect is eager to conduct a Security Lifecycle Review (SLR) with the aid of the Palo ...
- Q141. An administrator has a requirement to export decrypted traffic from the Palo Alto Networks...
- Q142. Which method will dynamically register tags on the Palo Alto Networks NGFW?...
- Q143. Refer to the exhibit. (Exhibit) Using the above screenshot of the ACC, what is the best me...
- Q144. Users within an enterprise have been given laptops that are joined to the corporate domain...
- Q145. What are the two behavior differences between Highlight Unused Rules and the Rule Usage Hi...
- Q146. Given the following table. (Exhibit) Which configuration change on the firewall would caus...
- Q147. After pushing a security policy from Panorama to a PA-3020 firwall, the firewall administr...
- Q148. An administrator allocates bandwidth to a Prisma Access Remote Networks compute location w...
- Q149. On the NGFW. how can you generate and block a private key from export and thus harden your...
- Q150. An administrator is configuring an IPSec VPN to a Cisco ASA at the administrator's home an...
- Q151. Refer to the exhibit. (Exhibit) Which certificates can be used as a Forward Trust certific...
- Q152. A speed/duplex negotiation mismatch is between the Palo Alto Networks management port and ...
- Q153. Which prerequisite must be satisfied before creating an SSH proxy Decryption policy?...
- Q154. Place the steps in the WildFire process workflow in their correct order. (Exhibit)...
- Q155. An administrator just submitted a newly found piece of spyware for WildFire analysis. The ...
- Q156. Decrypted packets from the website https://www.microsoft.com will appear as which applicat...
- Q157. An administrator is using Panorama and multiple Palo Alto Networks NGFWs. After upgrading ...
- Q158. A Security policy rule is configured with a Vulnerability Protection Profile and an action...
- Q159. Which CLI command displays the physical media that are connected to ethernetl/8?...
- Q160. Which three function are found on the dataplane of a PA-5050? (Choose three)...
- Q161. Using multiple templates in a stack to manage many firewalls provides which two advantages...
- Q162. Which three settings are defined within the Templates object of Panorama? (Choose three.)...
- Q163. Refer to the exhibit. (Exhibit) A web server in the DMZ is being mapped to a public addres...
- Q164. Which statement accurately describes service routes and virtual systems?...
- Q165.
- Q166. What type of address object would be useful for internal devices where the addressing stru...
- Q167. A customer wants to set up a VLAN interface for a Layer 2 Ethernet port. Which two mandato...
- Q168. Which logs enable a firewall administrator to determine whether a session was decrypted?...
- Q169. Refer to the exhibit. (Exhibit) Based on the screenshots above what is the correct order i...
- Q170. A customer wants to set up a VLAN interface for a Layer 2 Ethernet port. Which two mandato...
- Q171. Which virtual router feature determines if a specific destination IP address is reachable?...
- Q172. Which version of GlobalProtect supports split tunneling based on destination domain, clien...
- Q173. An administrator has 750 firewalls The administrator's central-management Panorama instanc...
- Q174. View the GlobalProtect configuration screen capture. What is the purpose of this configura...
- Q175. View the GlobalProtect configuration screen capture. (Exhibit) What is the purpose of this...
- Q176. The web server is configured to listen for HTTP traffic on port 8080. The clients access t...
- Q177. Refer to the exhibit. (Exhibit) An administrator is using DNAT to map two servers to a sin...
- Q178. Which statement is true regarding a Best Practice Assessment?...
- Q179. If an administrator does not possess a website's certificate, which SSL decryption mode wi...
- Q180. The web server is configured to listen for HTTP traffic on port 8080. The clients access t...
- Q181. A bootstrap USB flash drive has been prepared using a Windows workstation to load the init...
- Q182. An administrator is configuring an IPSec VPN to a Cisco ASA at the administrator's home an...
- Q183. What are three possible verdicts that WildFire can provide for an analyzed sample? (Choose...
- Q184. An administrator deploys PA-500 NGFWs as an active/passive high availability pair. The dev...
- Q185. A distributed log collection deployment has dedicated log Collectors. A developer needs a ...
- Q186. View the GlobalProtect configuration screen capture. What is the purpose of this configura...
- Q187. An administrator has left a firewall to use the default port for all management services. ...
- Q188. Which three options are supported in HA Lite? (Choose three.)...
- Q189. How would an administrator monitor/capture traffic on the management interface of the Palo...
- Q190. What is exchanged through the HA2 link?
- Q191. An administrator needs to troubleshoot a User-ID deployment The administrator believes tha...
- Q192. An administrator has been asked to configure a Palo Alto Networks NGFW to provide protecti...
- Q193. An administrator accidentally closed the commit window/screen before the commit was finish...
- Q194. Which Security policy rule will allow an admin to block facebook chat but allow Facebook i...
- Q195. Which Palo Alto Networks VM-Series firewall is valid?...
- Q196. Using multiple templates in a stack to manage many firewalls provides which two advantages...
- Q197. A company has a policy that denies all applications it classifies as bad and permits only ...
- Q198. During the packet flow process, which two processes are performed in application identific...
- Q199. Which three statements accurately describe Decryption Mirror? (Choose three.)...
- Q200. A firewall should be advertising the static route 10 2 0 0/24 into OSPF The configuration ...
- Q201. Which data flow describes redistribution of user mappings?...
- Q202. An engineer needs to permit XML API access to a firewall for automation on a network segme...
- Q203. A firewall administrator requires an A/P HA pair to fail over more quickly due to critical...
- Q204. What is the purpose of the firewall decryption broker?...
- Q205. An administrator has a PA-820 firewall with an active Threat Prevention subscription The a...
- Q206. Refer to the exhibit. (Exhibit) Which will be the egress interface if the traffic's ingres...
- Q207. Refer to the exhibit. (Exhibit) Which certificates can be used as a Forwarded Trust certif...
- Q208. Which PAN-OS® policy must you configure to force a user to provide additional credentials ...
- Q209. Please match the terms to their corresponding definitions. (Exhibit)...
- Q210. What are two common reasons to use a "No Decrypt" action to exclude traffic from SSL decry...
- Q211. YouTube videos are consuming too much bandwidth on the network, causing delays in mission-...
- Q212. When configuring the firewall for packet capture, what are the valid stage types?...
- Q213. To protect your firewall and network from single source denial of service (DoS) attacks th...
- Q214. SD-WAN is designed to support which two network topology types? (Choose two.)...
- Q215. An organization is building a Bootstrap Package to deploy Palo Alto Networks VM-Series fir...
- Q216. An administrator has enabled OSPF on a virtual router on the NGFW. OSPF is not adding new ...
- Q217. An administrator deploys PA-500 NGFWs as an active/passive high availability pair. The dev...
- Q218. Based on PANW Best Practices for Planning DoS and Zone Protection, match each type of DoS ...
- Q219. An administrator accidentally closed the commit window/screen before the commit was finish...
- Q220. Which prerequisite must be satisfied before creating an SSH proxy Decryption policy?...
- Q221. An engineer has discovered that certain real-time traffic is being treated as best effort ...
- Q222. When a malware-infected host attempts to resolve a known command-and-control server, the t...
- Q223. What does SSL decryption require to establish a firewall as a trusted third party and to e...
- Q224. Which three user authentication services can be modified to provide the Palo Alto Networks...
- Q225. What are three reasons why an installed session can be identified with the "application in...
- Q226. An administrator wants to upgrade a firewall HA pair to PAN-OS 10.1 The firewalls are curr...
- Q227. An administrator wants multiple web servers in the DMZ to receive connections initiated fr...
- Q228. Refer to the exhibit. A web server in the DMZ is being mapped to a public address through ...
- Q229. In a virtual router, which object contains all potential routes?...
- Q230. Which User-ID method maps IP address to usernames for users connecting through a web proxy...
- Q231. An administrator deploys PA-500 NGFWs as an active/passive high availability pair. The dev...

[×]
Download PDF File
Enter your email address to download PaloAltoNetworks.PCNSE.v2023-04-17.q231.pdf

