Join the discussion
Question 1/169
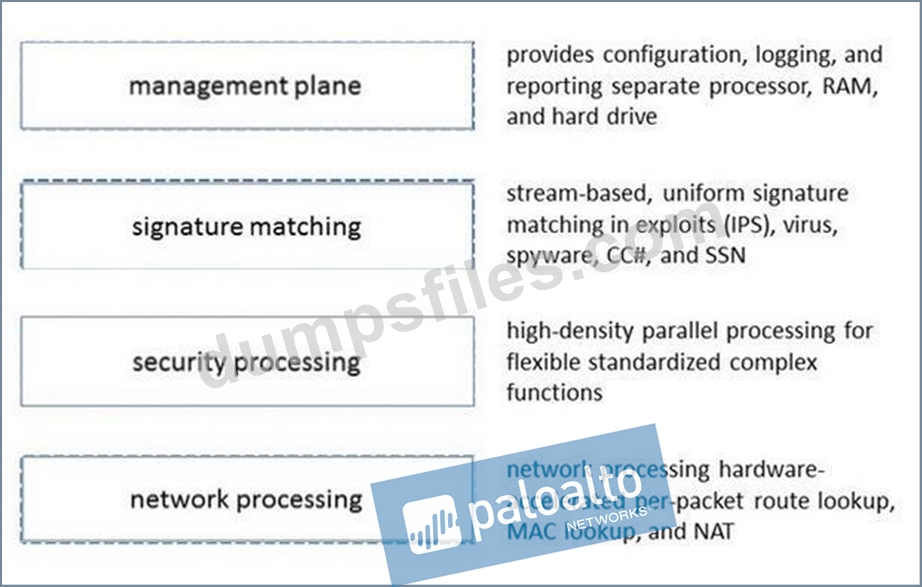
Please match the terms to their corresponding definitions.


Correct Answer:
Explanation
Graphical user interface Description automatically generated with medium confidence
Add Comments
- Other Question (169q)
- Q1. Please match the terms to their corresponding definitions. (Exhibit)...
- Q2. An administrator logs in to the Palo Alto Networks NGFW and reports that the WebUI is miss...
- Q3. A network administrator is troubleshooting an issue with Phase 2 of an IPSec VPN tunnel. T...
- Q4. A superuser is tasked with creating administrator accounts for three contractors. For comp...
- Q5. View the GlobalProtect configuration screen capture. (Exhibit) What is the purpose of this...
- Q6. Which statement regarding HA timer settings is true?...
- Q7. A company hosts a publically accessible web server behind a Palo Alto Networks next genera...
- Q8. An engineer has been given approval to upgrade their environment 10 PAN-OS 10 2 The enviro...
- Q9. Review the screenshot of the Certificates page. (Exhibit) An administrator tor a small LLC...
- Q10. The firewall determines if a packet is the first packet of a new session or if a packet is...
- Q11. An engineer is monitoring an active/active high availability (HA) firewall pair. Which HA ...
- Q12. A company is deploying User-ID in their network. The firewall learn needs to have the abil...
- Q13. Refer to the exhibit. (Exhibit) Based on the screenshots above what is the correct order i...
- Q14. A prospect is eager to conduct a Security Lifecycle Review (SLR) with the aid of the Palo ...
- Q15. What file type upload is supported as part of the basic WildFire service?...
- Q16. What is a correct statement regarding administrative authentication using external service...
- Q17. A company wants to install a PA-3060 firewall between two core switches on a VLAN trunk li...
- Q18. When is the content inspection performed in the packet flow process?...
- Q19. A distributed log collection deployment has dedicated Log Collectors. A developer needs a ...
- Q20. Review the images. A firewall policy that permits web traffic includes the global-logs pol...
- Q21. An administrator needs to upgrade an NGFW to the most current version of PAN-OS® software....
- Q22. An engineer configures a specific service route in an environment with multiple virtual sy...
- Q23. The firewall identifies a popular application as an unknown-tcp. Which two options are ava...
- Q24. Which operation will impact the performance of the management plane?...
- Q25. A network security engineer must implement Quality of Service policies to ensure specific ...
- Q26. A firewall administrator requires an A/P HA pair to fail over more quickly due to critical...
- Q27. Click the Exhibit button (Exhibit) An administrator has noticed a large increase in bittor...
- Q28. Which two profiles should be configured when sharing tags from threat logs with a remote U...
- Q29. A firewall administrator has been tasked with ensuring that all Panorama configuration is ...
- Q30. Which Palo Alto Networks VM-Series firewall is valid?...
- Q31. An administrator has been asked to configure a Palo Alto Networks NGFW to provide protecti...
- Q32. Which Security policy rule will allow an admin to block facebook chat but allow Facebook i...
- Q33. Which two subscriptions are available when configuring panorama to push dynamic updates to...
- Q34. What are the three key components of a successful Three Tab Demo? (Select the three correc...
- Q35. An organization is interested in migrating from their existing web proxy architecture to t...
- Q36. What are three types of Decryption Policy rules? (Choose three.)...
- Q37. Information Security is enforcing group-based policies by using security-event monitoring ...
- Q38. An administrator has purchased WildFire subscriptions for 90 firewalls globally. What shou...
- Q39. Which prerequisite must be satisfied before creating an SSH proxy Decryption policy?...
- Q40. A company has a policy that denies all applications it classifies as bad and permits only ...
- Q41. Refer to the exhibit. (Exhibit) Which certificates can be used as a Forwarded Trust certif...
- Q42. An engineer configures a new template stack for a firewall that needs to be deployed. The ...
- Q43. Refer to the exhibit. A web server in the DMZ is being mapped to a public address through ...
- Q44. Which event will happen if an administrator uses an Application Override Policy?...
- Q45. Which data flow describes redistribution of user mappings?...
- Q46. Which method will dynamically register tags on the Palo Alto Networks NGFW?...
- Q47. Which function is handled by the management plane (control plane) of a Palo Alto Networks ...
- Q48. An administrator wants multiple web servers in the DMZ to receive connections initiated fr...
- Q49. An administrator creates an SSL decryption rule decrypting traffic on all ports. The admin...
- Q50. What is the purpose of the firewall decryption broker?...
- Q51. You have upgraded your Panorama and Log Collectors lo 10.2 x. Before upgrading your firewa...
- Q52. Why would a traffic log list an application as "not-applicable"?...
- Q53. An engineer configures SSL decryption in order to have more visibility to the internal use...
- Q54. A security engineer received multiple reports of an IPSec VPN tunnel going down the night ...
- Q55. An enterprise Information Security team has deployed policies based on AD groups to restri...
- Q56. A network security engineer configured IP multicast in the virtual router to support a new...
- Q57. A network administrator wants to deploy SSL Forward Proxy decryption. What two attributes ...
- Q58. A network security administrator wants to begin inspecting bulk user HTTPS traffic flows e...
- Q59. A company wants to install a PA-3060 firewall between two core switches on a VLAN trunk li...
- Q60. Refer to the exhibit. (Exhibit) Which certificates can be used as a Forwarded Trust certif...
- Q61. Which GlobalProtect gateway selling is required to enable split-tunneling by access route,...
- Q62. Refer to the diagram. (Exhibit) An administrator needs to create an address object that wi...
- Q63. SSL Forward Proxy decryption is configured but the firewall uses Untrusted-CA to sign the ...
- Q64. Which statement accurately describes service routes and virtual systems?...
- Q65. A bootstrap USB flash drive has been prepared using a Windows workstation to load the init...
- Q66. Which log type will help the engineer verify whether packet buffer protection was activate...
- Q67. A firewall administrator needs to check which egress interface the firewall will use to ro...
- Q68. Which three user authentication services can be modified to provide the Palo Alto Networks...
- Q69. When configuring the firewall for packet capture, what are the valid stage types?...
- Q70. View the GlobalProtect configuration screen capture. (Exhibit) What is the purpose of this...
- Q71. Which User-ID method should be configured to map IP addresses to usernames for users conne...
- Q72. An administrator wants multiple web servers in the DMZ to receive connections initiated fr...
- Q73. What happens when an A/P firewall pair synchronizes IPsec tunnel security associations (SA...
- Q74. In the following image from Panorama, why are some values shown in red? (Exhibit)...
- Q75. An administrator has a requirement to export decrypted traffic from the Palo Alto Networks...
- Q76. Refer to the diagram. (Exhibit) An administrator needs to create an address object that wi...
- Q77. If the firewall has the link monitoring configuration, what will cause a failover? (Exhibi...
- Q78. A network security administrator has an environment with multiple forms of authentication....
- Q79. A firewall is configured with SSL Forward Proxy decryption and has the following four ente...
- Q80. Which three actions can Panorama perform when deploying PAN-OS images to its managed devic...
- Q81. An administrator is attempting to create policies for deployment of a device group and tem...
- Q82. An administrator notices that an interface configuration has been overridden locally on a ...
- Q83. A network engineer troubleshoots a VPN Phase 2 mismatch and decides that PFS (Perfect Forw...
- Q84. Refer to exhibit. An organization has Palo Alto Networks NGFWs that send logs to remote mo...
- Q85. Please match the terms to their corresponding definitions. (Exhibit)...
- Q86. An organization has recently migrated its infrastructure and configuration to NGFWs, for w...
- Q87. Which CLI command displays the current management plane memory utilization?...
- Q88. Which item enables a firewall administrator to see details about traffic that is currently...
- Q89. In High Availability, which information is transferred via the HA data link?...
- Q90. An administrator is considering upgrading the Palo Alto Networks NGFW and central manageme...
- Q91. A remote administrator needs firewall access on an untrusted interface Which two component...
- Q92. Which two actions would be part of an automatic solution that would block sites with untru...
- Q93. Which option would an administrator choose to define the certificate and protocol that Pan...
- Q94. An administrator encountered problems with inbound decryption. Which option should the adm...
- Q95. When configuring a GlobalProtect Portal, what is the purpose of specifying an Authenticati...
- Q96. What is the purpose of the firewall decryption broker?...
- Q97. Which Zone Pair and Rule Type will allow a successful connection for a user on the Interne...
- Q98. A firewall engineer creates a new App-ID report under Monitor > Reports > Applicatio...
- Q99. (Exhibit) At which stage of the cyber-attack lifecycle would the attacker attach an infect...
- Q100. View the GlobalProtect configuration screen capture. What is the purpose of this configura...
- Q101. An administrator has left a firewall to use the default port for all management services. ...
- Q102. An administrator needs to assign a specific DNS server to one firewall within a device gro...
- Q103. A firewall has been assigned to a new template stack that contains both "Global" and "Loca...
- Q104. A session in the Traffic log is reporting the application as "incomplete." What does "inco...
- Q105. Which two statements correctly describe Session 380280? (Choose two.) (Exhibit)...
- Q106. A traffic log might list an application as "not-applicable" for which two reasons'? (Choos...
- Q107. Which DoS Protection Profile detects and prevents session exhaustion attacks against speci...
- Q108. An engineer is tasked with deploying SSL Forward Proxy decryption for their organization. ...
- Q109. An administrator encountered problems with inbound decryption. Which option should the adm...
- Q110. An administrator is using Panorama and multiple Palo Alto Networks NGFWs. After upgrading ...
- Q111. Refer to the image. (Exhibit) An administrator is tasked with correcting an NTP service co...
- Q112. Which authentication source requires the installation of Palo Alto Networks software, othe...
- Q113. Which three actions can Panorama perform when deploying PAN-OS images to its managed devic...
- Q114. A firewall administrator wants to avoid overflowing the company syslog server with traffic...
- Q115. Which type of interface does a firewall use to forward decrypted traffic to a security cha...
- Q116. The administrator has enabled BGP on a virtual router on the Palo Alto Networks NGFW, but ...
- Q117. A customer has an application that is being identified as unknown-top for one of their cus...
- Q118. The web server is configured to listen for HTTP traffic on port 8080. The clients access t...
- Q119. Which three file types can be forwarded to WildFire for analysis as a part of the basic Wi...
- Q120. An administrator needs to troubleshoot a User-ID deployment The administrator believes tha...
- Q121. An administrator accidentally closed the commit window/screen before the commit was finish...
- Q122. SSL Forward Proxy decryption is configured but the firewall uses Untrusted-CA to sign the ...
- Q123. A company.com wants to enable Application Override. Given the following screenshot: (Exhib...
- Q124. What would allow a network security administrator to authenticate and identify a user with...
- Q125. The GlobalProtect Portal interface and IP address have been configured. Which other value ...
- Q126. What is the best definition of the Heartbeat Interval?...
- Q127. An administrator has enabled OSPF on a virtual router on the NGFW. OSPF is not adding new ...
- Q128. What is exchanged through the HA2 link?
- Q129. A company requires that a specific set of ciphers be used when remotely managing their Pal...
- Q130. Which two options prevent the firewall from capturing traffic passing through it? (Choose ...
- Q131. Which data flow describes redistribution of user mappings?...
- Q132. During a laptop-replacement project, remote users must be able to establish a GlobalProtec...
- Q133. An administrator is configuring an IPSec VPN to a Cisco ASA at the administrator's home an...
- Q134. How can Panorama help with troubleshooting problems such as high CPU or resource exhaustio...
- Q135. An administrator is receiving complaints about application performance degradation. After ...
- Q136. An organization is building a Bootstrap Package to deploy Palo Alto Networks VM-Series fir...
- Q137. How would an administrator configure a Bidirectional Forwarding Detection profile for BGP ...
- Q138. What should an administrator consider when planning to revert Panorama to a pre-PAN-OS 8.1...
- Q139. Place the steps in the WildFire process workflow in their correct order. (Exhibit)...
- Q140. Where is information about packet buffer protection logged?...
- Q141. Refer to the exhibit. (Exhibit) An administrator is using DNAT to map two servers to a sin...
- Q142. What are two prerequisites for configuring a pair of Palo Alto Networks firewalls in an ac...
- Q143. A network design change requires an existing firewall to start accessing Palo Alto Updates...
- Q144. Site-A and Site-B have a site-to-site VPN set up between them. OSPF is configured to dynam...
- Q145. Which three user authentication services can be modified to provide the Palo Alto Networks...
- Q146. An engineer is in the planning stages of deploying User-ID in a diverse directory services...
- Q147. A Palo Alto Networks NGFW just submitted a file to WildFire for analysis. Assume a 5-minut...
- Q148. An engineer must configure a new SSL decryption deployment. Which profile or certificate i...
- Q149. Refer to the exhibit. (Exhibit) An organization has Palo Alto Networks NGFWs that send log...
- Q150. When configuring forward error correction (FEC) for PAN-OS SD-WAN, an administrator would ...
- Q151. A global corporate office has a large-scale network with only one User-ID agent, which cre...
- Q152. If an administrator wants to decrypt SMTP traffic and possesses the server's certificate, ...
- Q153. A network administrator troubleshoots a VPN issue and suspects an IKE Crypto mismatch betw...
- Q154. The firewall determines if a packet is the first packet of a new session or if a packet is...
- Q155. How does an administrator schedule an Applications and Threats dynamic update while delayi...
- Q156. Which three actions can Panorama perform when deploying PAN-OS images to its managed devic...
- Q157. What are three valid actions in a File Blocking Profile? (Choose three)...
- Q158. A Network Administrator wants to deploy a Large Scale VPN solution. The Network Administra...
- Q159. Place the steps in the WildFire process workflow in their correct order. (Exhibit)...
- Q160. Which three rule types are available when defining polices in Panorama? (Choose three.)...
- Q161. An administrator has been asked to configure a Palo Alto Networks NGFW to provide protecti...
- Q162. Which DoS protection mechanism detects and prevents session exhaustion attacks?...
- Q163. An administrator has left a firewall to use the default port for all management services. ...
- Q164. An administrator needs to upgrade a Palo Alto Networks NGFW to the most current version of...
- Q165. What is the best definition of the Heartbeat Interval?...
- Q166. A web server is hosted in the DMZ and the server is configured to listen for incoming conn...
- Q167. A company wants to implement threat prevention to take action without redesigning the netw...
- Q168. Which CLI command displays the current management plane memory utilization?...
- Q169. An administrator has a requirement to export decrypted traffic from the Palo Alto Networks...

[×]
Download PDF File
Enter your email address to download PaloAltoNetworks.PCNSE.v2024-07-26.q169.pdf

